Apache Httpd Traversal Vulnerability
Overview:
The Apache HTTP server is the most popular web server used on the Internet. The server is capable of being utilized with many different options and configurations. A wide variety of runtime loadable plug-in modules can be used to extend its functionality.
A directory traversal vulnerability exists in Apache httpd. The vulnerability is due to improper normalization of paths in the request URI.
A remote attacker could exploit the vulnerability by sending a crafted HTTP request to the target server. Successful exploitation would result in disclosure of the content of files outside the expected document root, or in the worst case, execution of arbitrary code under the security context of the server process.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2021-41773.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 9.3 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:F/RL:O/RC:C).
Base score is 10.0 (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 9.3 (E:F/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is functional.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
When httpd receives an HTTP request, it is handled by the ap_process_async_request() function. The request data is processed by the ap_process_request_internal() function. This function normalizes the path submitted in the request URI by calling the ap_normalize_path() function. This function normalizes the path submitted by decoding URL-encoded characters, collapsing multiple slash (‘/’) characters, and interpreting “../” by traversing to the parent directory in the path.
After the normalization function, the ap_run_translate_name() function is called, which calls translate_alias_redir(). This function calls try_alias_list(), which looks up any ScriptAlias entries in the httpd server configuration file that match the request URI. If a match is found, apr_filepath_merge() is called, which merges the server root path with the normalized path. The merged path is later saved to the filename field of the request_rec structure. Next, access permissions are checked by calling ap_run_access_checker_ex(), which looks up the appropriate Require entries in the httpd server configuration.
If access is allowed, the appropriate handler is invoked for processing the request. If the request URI path begins with “/cgi-bin/”, and the mod_cgi module is enabled in the server configuration, the cgi_handler() function is called to handle the request. This function uses the filename field of the request_rec structure to build an OS command and runs the command in a child process. Then, the HTTP POST request data submitted is sent to the created process as input.
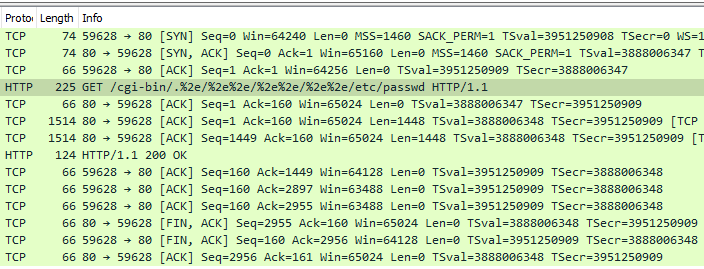
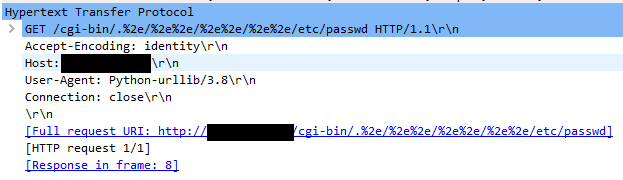
A directory traversal vulnerability exists in Apache httpd. The vulnerability is due to a flaw in the normalization of the path submitted in the URI of HTTP requests. The ap_normalize_path() function attempts to resolve “../” sequences in the path by traversing to the parent directory. However, if the second dot character (‘.’) in a “../” sequence is URL-encoded (i.e. “.%2e/”), the “../” sequence will not be interpreted and the sequence will remain in the normalized path. When this path is later merged with the server root path using the apr_filepath_merge() function, the resulting path saved to the filename field of the request_rec structure could traverse beyond the server root path. If access is granted to the server’s root directory and the mod_cgi module is enabled, an arbitrary executable on the server can be called, leading to arbitrary code execution.
A remote attacker could exploit this vulnerability by sending a request with a crafted URI to the target service. Successful exploitation could lead to exposure of the contents of arbitrary files on the server. If the mod_cgi module is enabled, exploitation could lead to execution of arbitrary code on the target server.
Triggering the Problem:
• The target system must have the vulnerable product installed and running.
• The attacker must have network connectivity to the affected ports.
• Permissions must be granted to the server’s root directory in the httpd.conf configuration file.
• Arbitrary code on the target server, the mod_cgi module must be enabled in the httpd.conf configuration file.
Triggering Conditions:
The attacker sends an HTTP request with a maliciously crafted URI path. The vulnerability is triggered when the server attempts to process the HTTP request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP, over port 80/TCP
• HTTPS, over port 443/TCP
Http Request:
Http Request In Text:
Password File:
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2140 Web Application Directory Traversal 48
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor-supplied patch to eliminate this vulnerability.
• Filtering traffic based on the signature above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory