Apache Airflow DAG Injection Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
Apache Airflow is an open-source workflow management platform. Apache Airflow is a flexible, scalable workflow automation and scheduling system for authoring and managing Big Data processing pipelines. Written in Python, the project is highly extensible and able to run tasks written in other languages, allowing integration with commonly used architectures and projects such as AWS S3, Docker, Apache Hadoop HDFS, Apache Hive, Kubernetes, MySQL, Postgres, Apache Zeppelin, and more.
Airflow originated at Airbnb in 2014 and was submitted to the Apache Incubator March 2016. The Apache Software Foundation (ASF), the all-volunteer developers, stewards, and incubators of more than 350 Open Source projects and initiatives, announced Apache® Airflow™ as a Top-Level Project (TLP).
A OS command injection vulnerability has been reported in Apache Airflow. This vulnerability is due to improper input validation for parameters for directed acyclic graphs (DAGs).
A remote, authenticated attacker could exploit this vulnerability by sending a crafted request to the target server. Successfully exploiting this vulnerability could result in OS command injection.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-24288.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.6 (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C).
Base score is 9.9 (AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is low.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.6 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
Airflow is designed under the principle of “configuration as code”. While other “configuration as code” workflow platforms exist using markup languages like XML, using Python allows developers to import libraries and classes to help them create their workflows. Apache Airflow utilizes the Django web application framework that implements a model-template-views (MTV) architectural pattern.
Directed Acyclic Graphs (DAGs) are collections of tasks users are able to execute; organized in a way that reflects their relationships and dependencies. Airflow uses directed acyclic graphs (DAGs) to manage workflow. There are a number of operations that can be performed including: triggering a DAG task, selecting a graph, viewing trees, deleting DAGs, and viewing code. The Base Airflow install includes examples of DAGs to demonstrate various features inside its package installer.
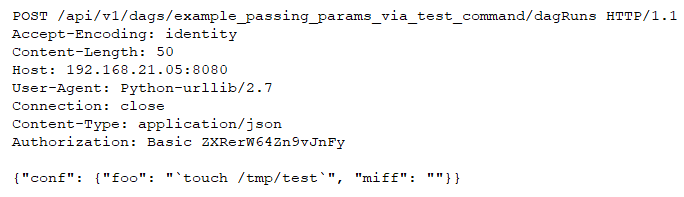
The example DAG (example_passing_params_via_test_command), shows a templated command with arguments using echo to print a string. The raw arguments of “foo” and “miff” are added to a flat command string and passed to the BashOperator class to execute a Bash command.
Triggering the Problem:
• The target host must have the affected version of the product installed and running.
• The attacker must have network access to the target system.
• The vulnerable DAG must be un-paused.
• The attacker must have access to an account with the RESOURCE_DAG_RUN permission
Triggering Conditions:
A malicious POST request is sent to the target server to run the vulnerable DAG.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2606 Apache Airflow DAG Command Injection 1
• IPS: 2607 Apache Airflow DAG Command Injection 2
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Upgrading the product to a non-vulnerable version.
• Filtering traffic based on the signatures above.
• Deleting the vulnerable DAG.
• Minimizing the number of users with the RESOURCE_DAG_RUN permission.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory