Another ransomware possibly belonging to the Revil ransomware group seen actively spreading in the wild
The SonicWall Capture Labs Research team has been observing a massive increase in ransomware attacks with increasingly targeted attacks hitting mostly critical infrastructures. With companies willing to pay millions in ransom payment to restore operations, the ransomware industry has never been more lucrative for cybercriminals. This week we have observed a spike in detections for a somewhat small player in the ransomware world. We have first spotted Prometheus ransomware in February and have not seen a lot of action until this week.
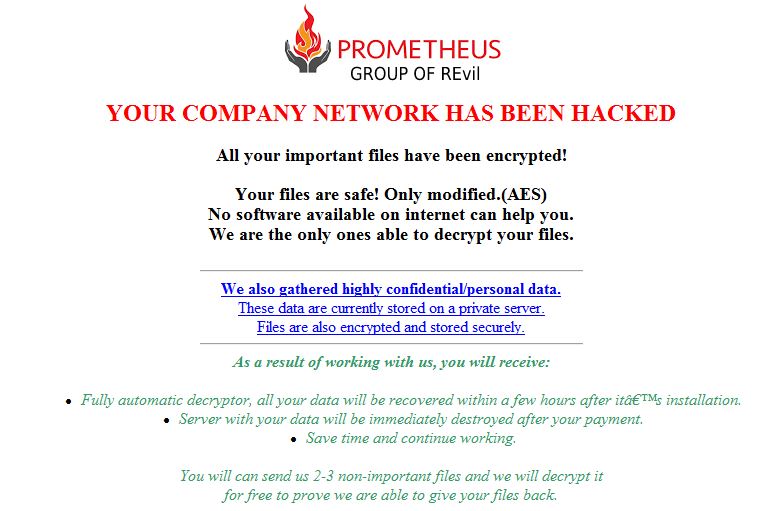
Interestingly, with Revil Ransomware in spotlight for which a lot of the high profile ransomware attacks have been attributed to lately, Prometheus ransomware claims to be from the same cybercriminal group. We have no proof that this is true, however.
Infection Cycle:
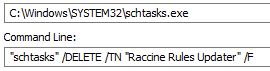
Upon execution, the first thing this ransomware does is to find and delete Raccine, an open source program that blocks ransomware from deleting shadow copies of a system’s data – a very common ransomware behavior. It employs taskill.exe to kill the Raccine executable, if it happens to be present in the system as well as delete any Raccine-related registry values.
![]()
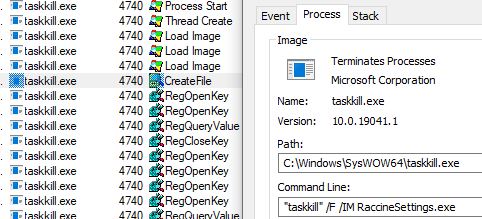
It then continues to kill other running processes using taskkill.exe including Microsoft Office processes like winword.exe, excel, mspub and visio, sql database related processes like sqlservice.exe, dbeng50.exe, mysqld.exe, among many others.
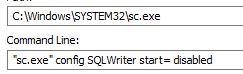
It also employs sc.exe to configure certain system services such as “SQLwriter start” to disable the functionality to be able to create backup and restore SQL Server data through the Volume Shadow Copy Service.
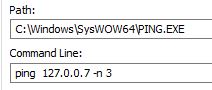
To ensure network connectivity it pings a loopback address 127.0.0.7
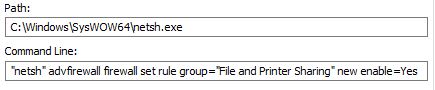
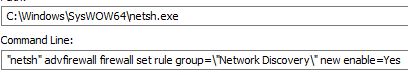
It also executes netsh.exe to run commands to alter the firewall settings to allow the infected system to be discoverable within the network and to allow for files and printer sharing.
Once target files have been encrypted, it displays an alert on the system tray and also opens an hta file with instructions on how to pay and retrieve files. The header of the instructions imparts that Prometheus belongs to the well-known Revil ransomware group.
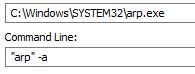
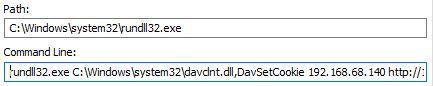
Another similar sample that we analyzed appears to be a more beefy program with more functionalities such as running commands to check the ARP table which can possibly be used for ARP attacks.
Also running a powershell command to delete all volume shadow copies.
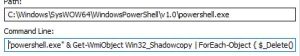
And also trying to configure and login to the local router admin page using additional dropped components.
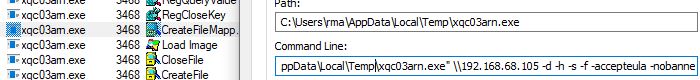
This newer version also provides additional ways to reach the ransomware authors outside of the Tor browser.
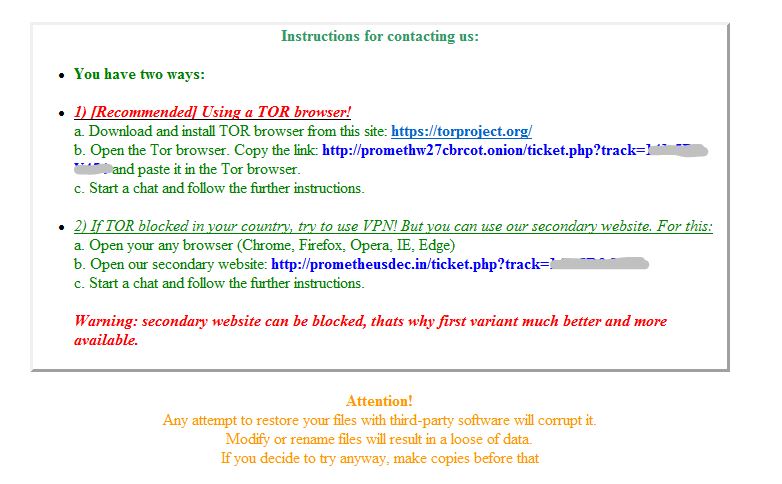
This goes to show that we will mostly likely see more from this ransomware group because they have been continuously improving their program with more robust functionalities to improve infection and possibly evade detection.
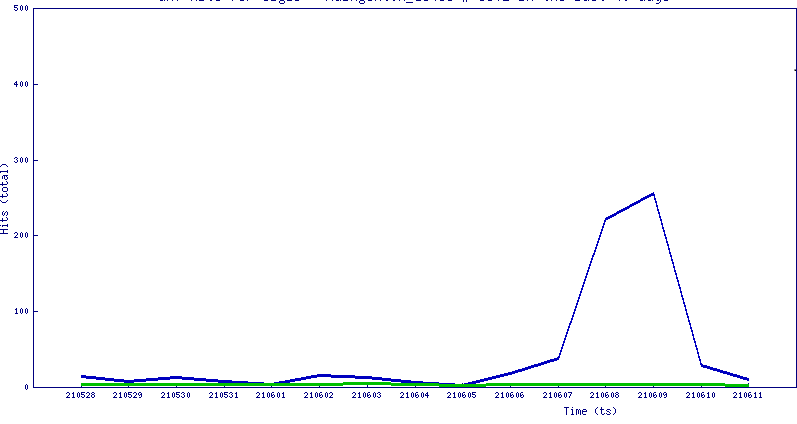
This week, we have noticed an uptick in detection for this particular ransomware.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Prometheus.RSM (Trojan)
- GAV: Prometheus.RSM_1 (Trojan)
- GAV: Prometheus.RSM_2 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.