AndroidLocker ransomware targeting android phones (May 15, 2014))
The Dell SonicWall Threats Research Team observed reports of an Android malware that locks up mobile devices until the victims pay a ransom to unlock the phone, called AndroidLocker. The message displayed looks like a warning from FBI for viewing, storage, and/or dissemination of banned pornography (child pornography/zoophilia/rape etc) to scare the victim and ask for ransom.
Infection Cycle
Before installation the app requests for the following permissions:
- receive_boot_completed (automatically start at boot)
- internet (full Internet access)
- wake_lock (prevent phone from sleeping)
- read_phone_state (read phone state and identity)
These permissions allow the application to access sensitive user information such as the serial number, phone number, etc.
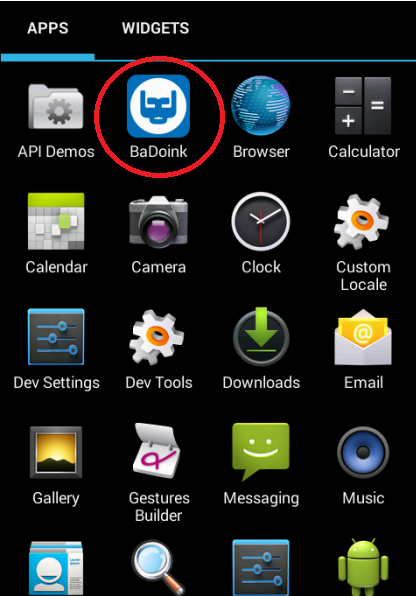
After installation, the application appears with a fake name “BaDoink”. Once the user opens the application, it will trigger the ransomware locking activity displaying the fake FBI alert. The users falling prey to these scare tactics will end up paying the ransom amount in order to avoid the charges and to get their phone unlocked. The malware leverages Geolocation API to display the warning tailored to the place the victim resides in.


Looking at AndroidManifest.xml, since it has the BootstrapReceiver set to the highest priority of 999, it would not allow any other application to run on the phone.

It sets an alarm to invoke com.android.ScheduleLockReceiver and com.android.SheduleUnlockReceiver periodically:

It also tries to connect to the following domains:
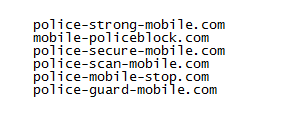
During our analysis, the sample tried to communicate with police-strong-mobile.com.

It steals the device information and connects to the above domain to display the lock screen:

The lock page is obtained from this server as shown below:

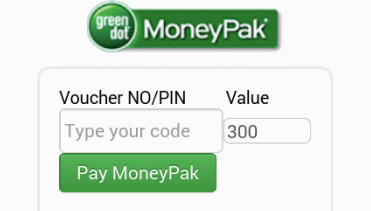
It displays that the amount of fine is 300$. You can settle the fine with MoneyPak xpress Packet vouchers at retail stores such as 7Eleven, Walmart, Kmart, Walgreens, CVS.
We are seeing an increasing number of malware families starting to target Mobile devices in addition to personal computers. This is the first instance we saw from the AndroidLocker Ransomware family which is the latest addition to the fast growing list of mobile malware families. Users are advised to be extremely cautious when installing applications from non-trusted third party sources.
Dell SonicWALL Gateway AntiVirus provides protection against this threat with the following signature:
- GAV: AndroidOS.Koler.A (Trojan)




