Android ransomware purports to be a free social media follower application
Sonicwall Capture Labs Threat Research team has observed many Android locker ransomware which asks to communicate using social media platforms. There is no assurance of getting the key even after paying the ransom amount, they just use these apps for monetary gain. Some of the applications look like free social media follower apps but are ransomware as shown below.
![]() Figure 1: Ransomware App Icons
Figure 1: Ransomware App Icons
All these malicious apps are recently submitted over malware sharing platforms like Virus Total.
 Figure 2: VirusTotal submission history
Figure 2: VirusTotal submission history
Infection Cycle:
Major permissions used in these apps are mentioned below:
- SYSTEM_ALERT_WINDOW
- RECEIVE_BOOT_COMPLETED
- SET_WALLPAPER
- READ_EXTERNAL_STORAGE
- WRITE_EXTERNAL_STORAGE
- READ_CONTACTS
- READ_SMS
- ACCESS_FINE_LOCATION
- WAKE_LOCK
- INTERNET
- REQUEST_INSTALL_PACKAGE
- CAMERA
Permission “SYSTEM_ALERT_WINDOW“ is used to display overlay windows above all activity windows in order to show ransom notes.
After installation app is not visible on the app drawer, to view installed app information we need to go into settings->Apps
Figure 3: Malicious app visible under settings
In the manifest file, “android.intent.category.LAUNCHER” is not set in MainActivity as shown below, which means that this application does not have a desktop startup icon.
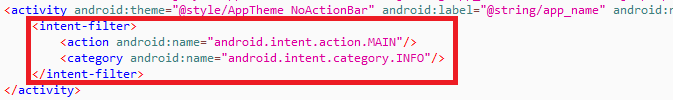 Figure 4: Main activity launcher missing
Figure 4: Main activity launcher missing
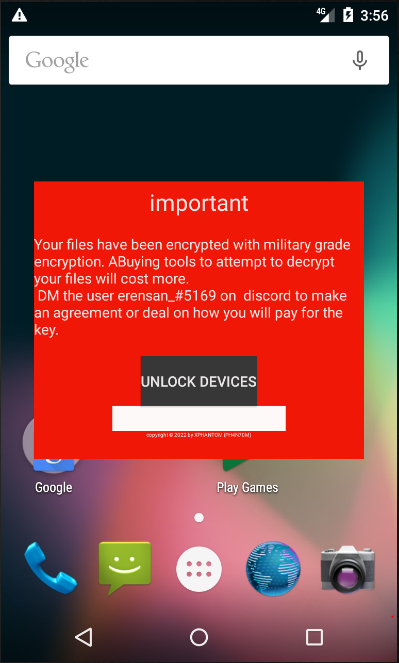
Malicious application launches after “ACTION_BOOT_COMPLETED” system event which is fired once the Android system has completed the boot process, sets a lock screen with a ransom note and the user is not able to access the device.
On further investigation of malicious code, each malicious file has a different ransom note and different keys which are present in code itself under “password” field. No actual encryption of any file present on the device takes place except by locking the screen.
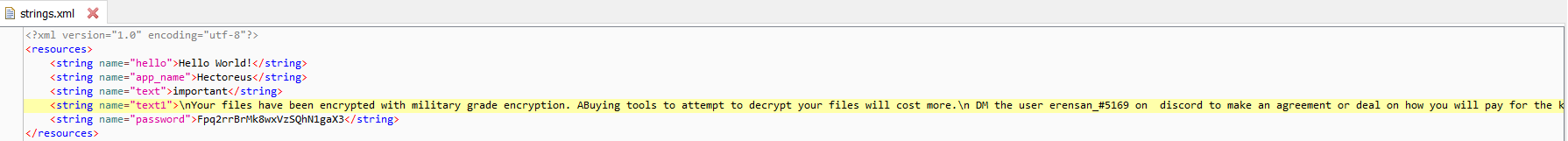 Figure 6: Password and Ransom note present in code
Figure 6: Password and Ransom note present in code
SonicWall Capture Labs provides protection against this threat via the SonicWall Capture ATP w/RTDMI.
Indicators of Compromise (IOC):
11a11a11a266f9d3858d1b52aca73b701406cbc587bf52a5256c20452d574d0a
193c8bc1f44cf310e670c0a4a9e19f9ad35afaac63eb549f9cc8dafa240555af
2cd6920661eec231b66ac3601ca380ba846490c8f535b903d3844326084ac490
2da6a8f85888d39c3a45b6d6367492e67243e985ef8bc4dc441fd66ffcbe3d9c
ac70993fb26bd4590d3656a4b6ba1e0787a9c524ed5ed5592663a6d8c05c32a1
ec38798940dbab431f3dacab74267b143e206ed8e3fc406be90125825198576a