Android banking trojan targets more than 450 apps
SonicWall Capture Labs Threats Research team yet again observed malicious Android banking trojans that target a large number of financial apps. This time the malicious app is spreading by masquerading the Austrain PayLife bank app.
Sample Details:
- Application Name: PayLife Kartensicherheit
- Package Name: muffin.limit.two
- Md5: 670e49e6cdb47f8e6121fc706b2c6886
Infection Cycle
Upon installation the application appears in the app drawer as follows:
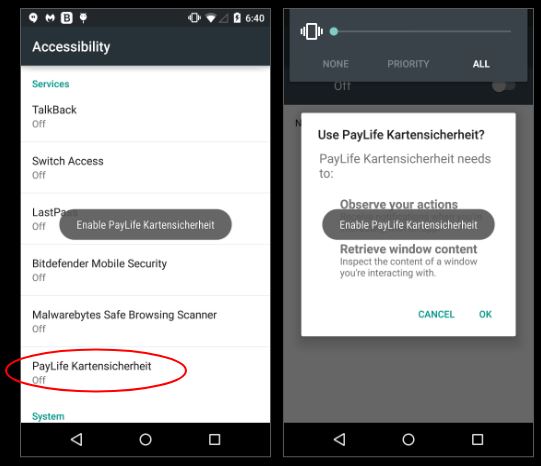
Once executed, the application icon disappears from the app drawer giving the victim an impression that the application is no more present on the device. Next, it requests for Accessibility services permission from the victim:
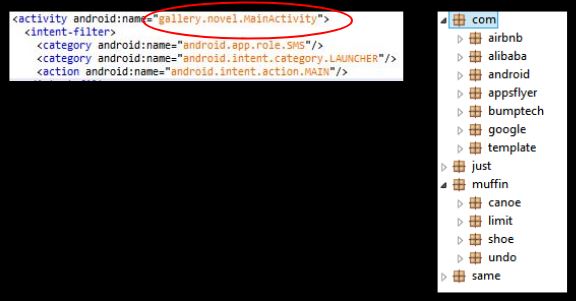
Upon checking the AndroidManifest.xml file for the main activity, we see an entry for an activity that is not visible in the source code:
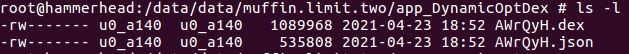
But on running the application on the device a few files are dropped in the folder app_DynamicOptDex. The sample we analyzed dropped the following interesting files:
- AWrQyH.dex
- AWrQyH.json
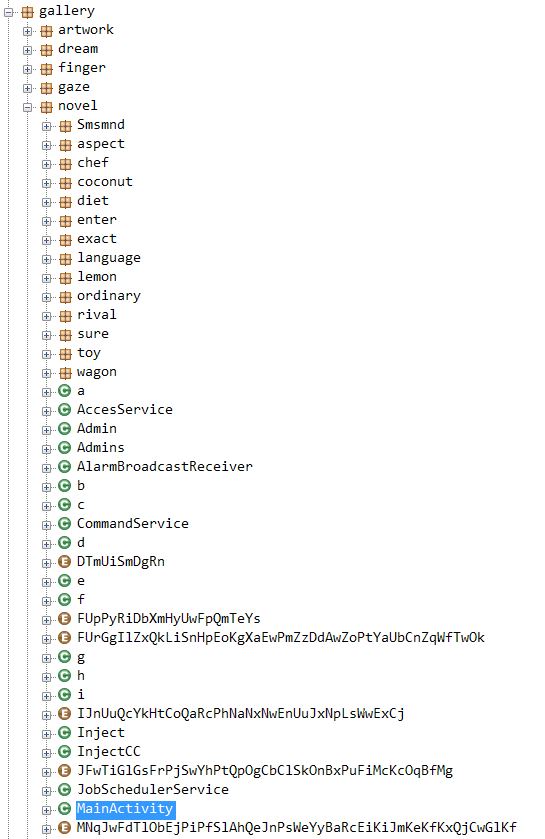
Within name.json file which is a .dex fiel in reality, we get the files containing malicious code including the main activity that was not visible earlier:
The malware is capable of accepting and executing the following commands:
- Send_SMS
- Flood_SMS
- Download_SMS
- Spam_on_contacts
- Change_SMS_Manager
- Run_App
- StartKeyLogs
- StopKeyLogs
- StartPush
- StopPush
- Hide_Screen_Lock
- Unlock_Hide_Screen
- Admin
- Profile
- Start_clean_Push
- Stop_clean_Push
Based on the commands and functionality, it appears that this malware is capable of carrying out a number of dangerous actions from the infected device:
- Critical SMS related actions
- Capture victim keystrokes
- Send SMS messages to contacts, this may include the ability to spread the infection to people in contacts
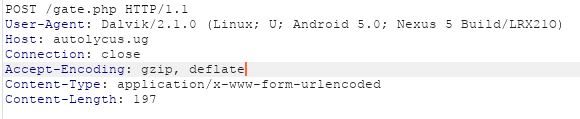
The malware we analyzed communicates with a hardcoded server – autolycus.ug
During our analysis the malware communicated with the server by sending encrypted data at gate.php. However we did not receive any communication back from the server:
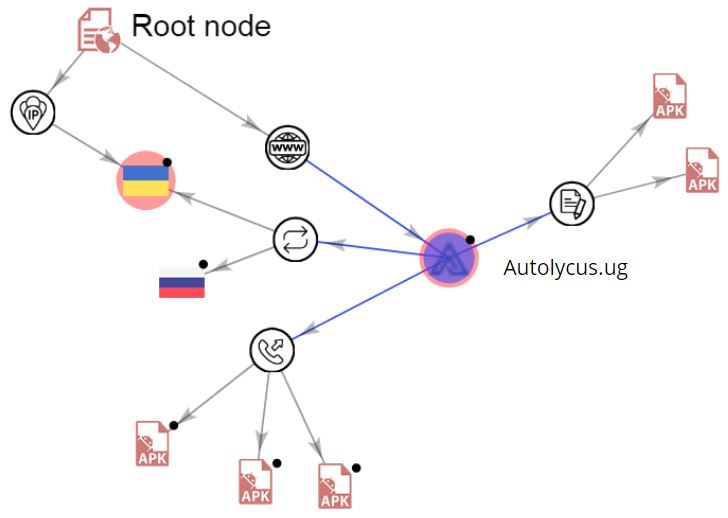
We observed the following VirusTotal graph for this domain:
The source code for this app contains a list of apps that are monitored by this malware, this list of around 455 apps contains a majority of financial apps. Few of these targeted apps are listed below, the complete list can be obtained here:
- ar.com.santander.rio.mbanking
- at.volksbank.volksbankmobile
- au.com.bankwest.mobile
- com.bancomer.mbanking
- com.bankaustria.android.olb
- com.bankofqueensland.boq
- com.bbva.mobile.pt
- com.CredemMobile
- com.db.pbc.DBPay
- com.desjardins.mobile
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: AndroidOS.Banker.AL (Trojan)
Indicators of compromise (IOC’s):
- 670e49e6cdb47f8e6121fc706b2c6886
- 6fb48c0121f446c3010867f02e0b53ee
- e030c8ba233ea0b3b50daafbe54605a6