Aggressive Android adware communicates with a number of malicious domains
SonicWall Capture Labs Threats Research Team came across an adware that showed high network communication during its execution. This is typical behavior of an adware but this adware communicated with a number of malicious domains which peaked our interest.
Infection Cycle
- Read settings
- Write settings
- Write external storage
- Read sms
- Send sms
- Receive sms
- System alert window
- Receive boot completed
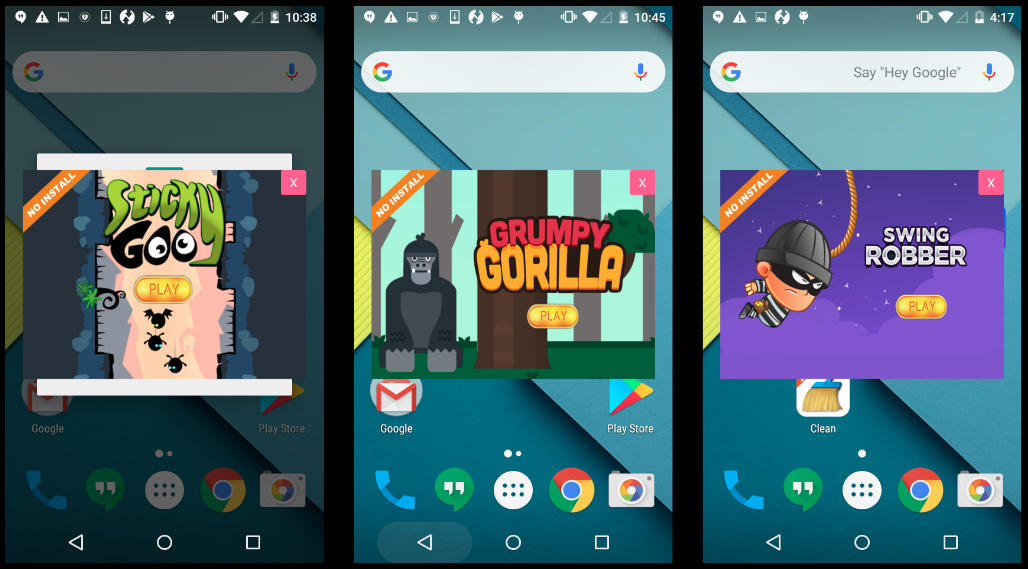
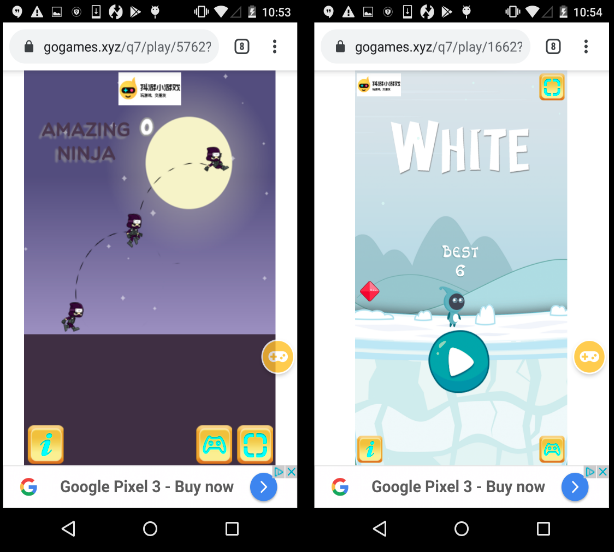
Soon after starting the adware app we began seeing ads that covered parts of the screen. We saw these advertisements at different times during our analysis. The advertisements were for casual games most of the times (more on this later in the blog).
Network Communications
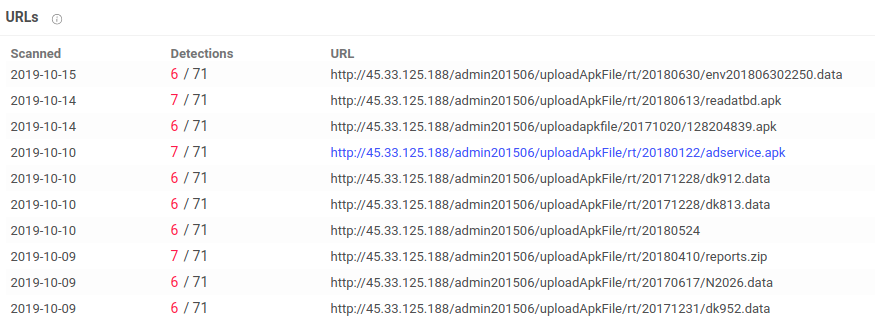
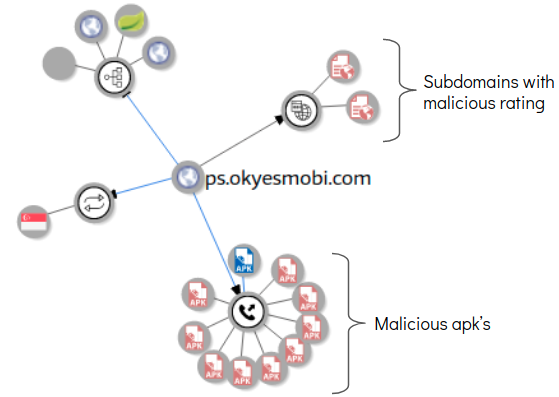
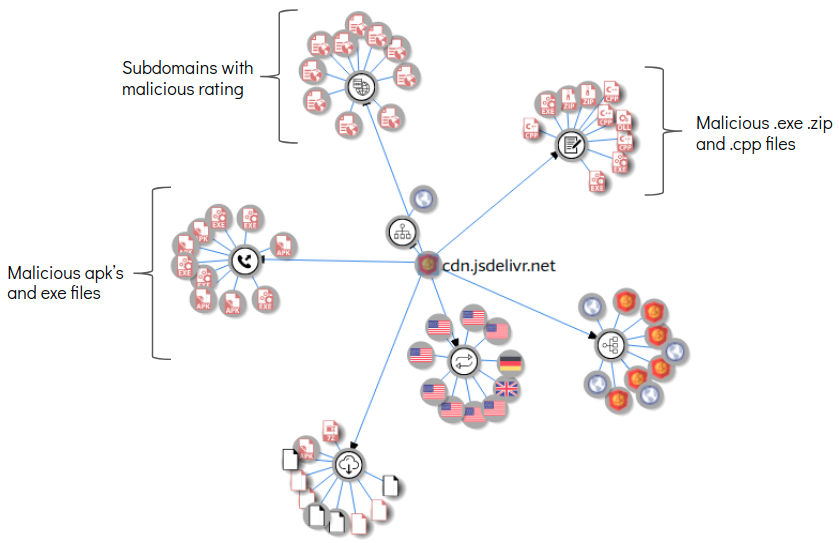
We saw a spike in network traffic once we started the app, a network capture revealed a multitude of domains that were contacted in quick successions. A number of these domains have been flagged as malicious on VirusTotal as few of these domains have connections with or are hosting malicious applications.
Below are few domains that were contacted and VirusTotal highlights about them:
45.33.125.188
139.162.141.85
cdn.jsdelivr.net
ps.okyesmobi.com:8802
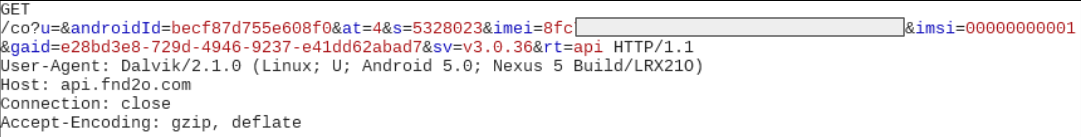
In one instance we saw the IMEI of our device was transmitted to one of the connected domains:
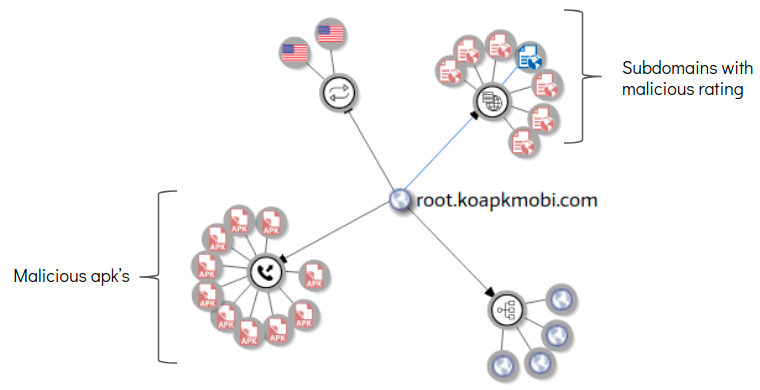
Some of the domains that were contacted host a number of malicious apk files, below are VirusTotal graphs for a few:
Spike in Network consumption
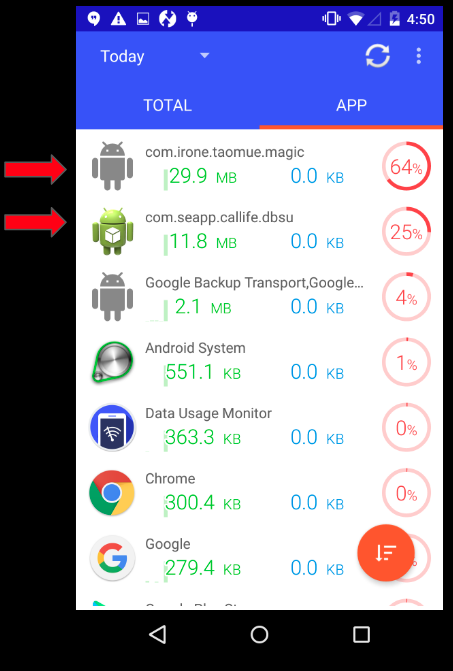
During our analysis we measured the network consumption from the infected device. Unsurprisingly, we saw high network consumption from the adware and apps installed by the adware as shown below:
This can be extremely annoying especially for folks with limited data capacity mobile plans.
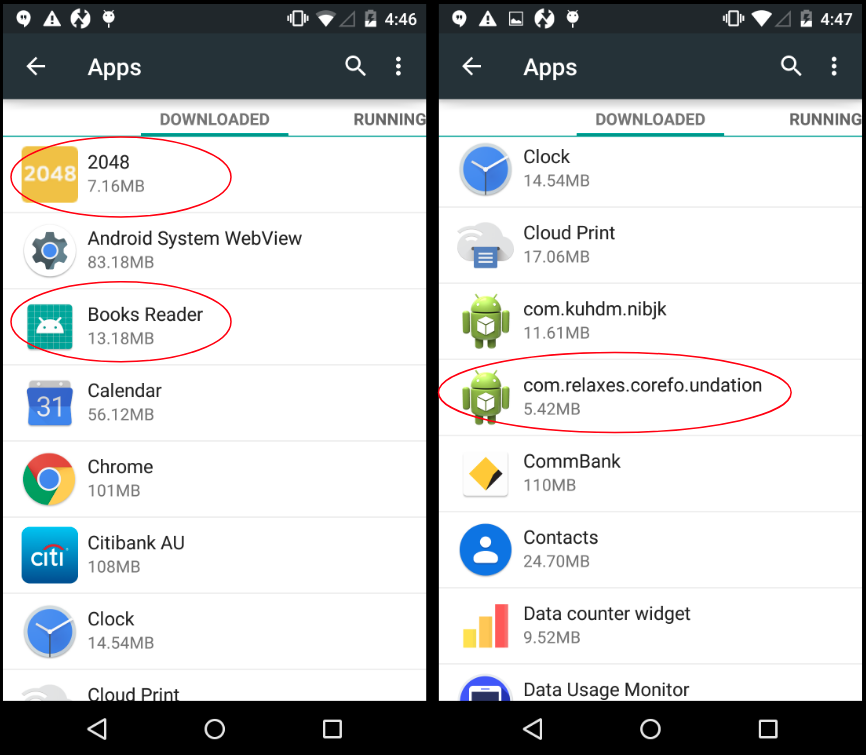
Installed apps and shortcuts
Gaming for ad profit
- The games are of the ‘endless runner’ category where the player accumulates points the more time he is alive
- Whenever the player loses, an advertisement is played
In short, the hosting company profits whenever the player loses. So how do they maximize their profits ? By making the games harder!
Compared to casual games like these, we observed the level of difficulty to be a bit steep in comparison. As a result we ended up losing more frequently which resulted in ads getting displayed each time we lost.
Overall this contributed towards an increase in network consumption and advertisement related profit for the uploaders.
Rooting mechanisms
The adware constantly requested superuser permissions once we started it:
One of the files present in the adware’s installed folder is a script file that contains code to root the device:
Closing thoughts
Overall this adware does a lot of activities after infecting a device. It displays advertisements, installs rogue apps, communicates with malicious domains and overall increases the network consumption of the device. We saw few instances where sensitive information from the device was leaked, but the fact that it communicates with domains with malicious content hosted on them is worrying.
Sonicwall Capture Labs provides protection against this threat with the following signature:
- AndroidOS.Adware.LO
Indicators Of Compromise (IOC’s):
- f1c7ff832393feac50d2ed3dc80ba3b8