Advantech R-SeeNet ping.php Command Injection Vulnerability
Overview:
Advantech R-SeeNet is a monitoring application that runs on a server and its job is to collect information from the routers, store it, process it and present it to a network administrator. R-SeeNet consists of two parts: R-SeeNet server and R-SeeNet PHP web-based application. R-SeeNet server is the non-visible part responsible for querying the routers and gathering information. The application also stores the recorded information into a MySQL database. R-SeeNet PHP web-based application is responsible to show both individual statistics and also whole network status.
A command injection vulnerability has been reported in Advantech R-SeeNet. The vulnerability is due to insufficient validation of the parameter in ping.php.
A remote, unauthenticated attacker can exploit this vulnerability by sending a crafted request to the target system. Successful exploitation could result in arbitrary command execution in the security context of web server on the target server.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2021-21805.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 9.4 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:P/RL:U/RC:C).
Base score is 10.0 (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 9.4 (E:P/RL:U/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept.
• The remediation level of this vulnerability is unavailable.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
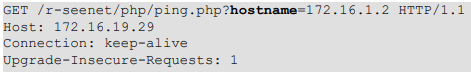
R-SeeNet web application server can send ping packets to other devices and get their status when receiving a request to the “ping.php” endpoint as below:
Where the hostname parameter value contains the IP address or host name of a remote device.
A command injection vulnerability exists in the Advantech R-SeeNet. When processing the request submitted to the ping.php endpoint, ping.php will first check if it is running on Windows platform. If not, it will construct a ping command-line string as below:
ping -c 5 -s 64 -t 64 hostname
Where the hostname is the value of the hostname request parameter. Then, it will use the PHP popen() function to execute the constructed ping command-line string and read its output.
However, the ping.php does not sanitize the hostname parameter before using it to construct the ping commandline string. An attacker can submit a malicious command embedded in the value of the hostname parameter to the target server. The malicious command will then be appended to the constructed ping command line string. This could allow for the execution of arbitrary commands on the underlying system when ping.php calls PHP popen() to run the ping command-line string.
A remote, unauthenticated attacker can exploit the vulnerability by sending crafted requests to the server. Successful exploitation could result in arbitrary command execution with web server privileges on the target server.
Triggering the Problem:
• The target system must have the vulnerable product installed and running.
• The attacker must have network connectivity to the affected ports.
Triggering Conditions:
The attacker sends an HTTP request containing maliciously crafted parameters to the target server. The vulnerability is triggered when the server processes the request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP, over port 80/TCP
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 15657 Advantech R-SeeNet ping.php Command Injection 1
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Blocking the affected ports from external network access if they are not required.
• Filtering traffic based on the signature above.
The vendor has not released any advisory regarding this vulnerability.