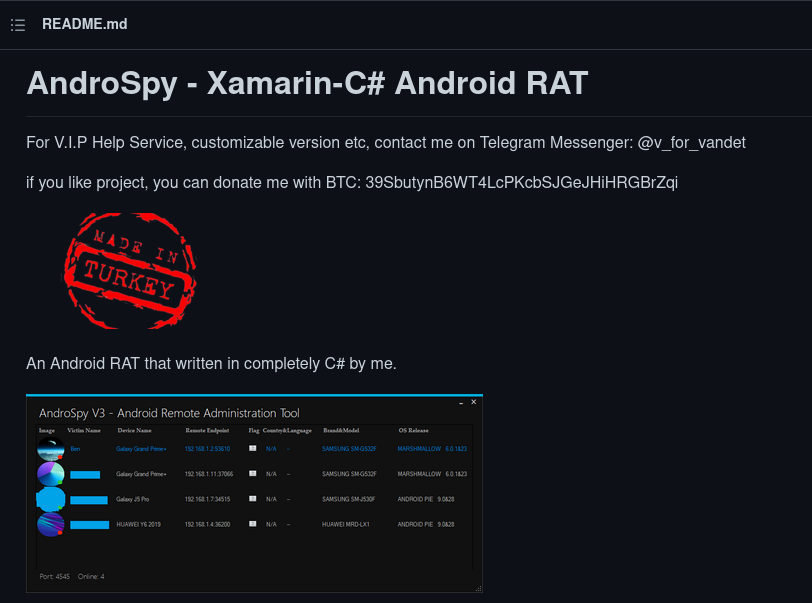
A Github repository exists for AndroSpy spyware for Android
SonicWall Threats Research team identified a version of AndroSpy in the wild. Interestingly, there exists a Github repository for this version of the malware. This repository was created a few months back and appears to be fairly active.
Sample specifics
- MD5: 1749d7830b1593fbe9eec1946002dee7
- Application Name: Critical Device Settings
- Package Name: com.kernel32.criticalprocess
This app requests a number of dangerous permissions, few of them are listed below:
- WRITE_EXTERNAL_STORAGE
- READ_EXTERNAL_STORAGE
- READ_CALL_LOG
- WRITE_CALL_LOG
- CAMERA
- READ_SMS
- ACCESS_FINE_LOCATION
- RECORD_AUDIO
- READ_CONTACTS
- WRITE_CONTACTS
- SEND_SMS
- BIND_DEVICE_ADMIN
- RECEIVE_SMS
- WRITE_SMS
- PROCESS_OUTGOING_CALLS
- DELETE_PACKAGES
- SYSTEM_ALERT_WINDOW
- ACCESSIBILITYSERVICE
This version of AndroSpy boasts a number of functionalities, some of them are listed below:
- Access camera
- Access files
- Live microphone
- Keylogger
- SMS manager
- Shell terminal
- Access contacts
- Call Logs
- Check installed apps
- Live screen
- Disable Google Play Protect
Similar threats
Searching for this app on Virustotal showed a number of related apps, some with different names and icons:
This indicates that this threat is being used and propagated with malicious intent. As mentioned earlier, the attacker server ad other configurations can be viewed under resources>res>values>strings
Additional observation
The github repository shows a BTC wallet address for donations towards this project:
Overall this is a spyware that is available on Github as a framework. This spyware is being used as legitimate application in some cases.
Sonicwall Capture Labs provides protection against this threat using the signature listed below:
- AndroidOS.Androspy.GT
Indicators of Compromise:
- 1749d7830b1593fbe9eec1946002dee7
- 603b7c441289ff7a15d3a458add66f2d
- 0e9d6812f7ed7f912fab2f74e143ea76
- 4f48d7d1258d52db555e0aae4b5136d6
- 93c0c8c706a219d4194110035898f36d