HermeticWiper data wiping malware targeting Ukrainian organizations
The SonicWall Capture Labs Threat Research team has analyzed a sample which is widely believed to be targeting Ukrainian organizations.
The malware sample is digitally signed issued under the company name ‘Hermetica Digital Ltd’. There is a possibility that the attacker might have used a shell company to issue this digital certificate.
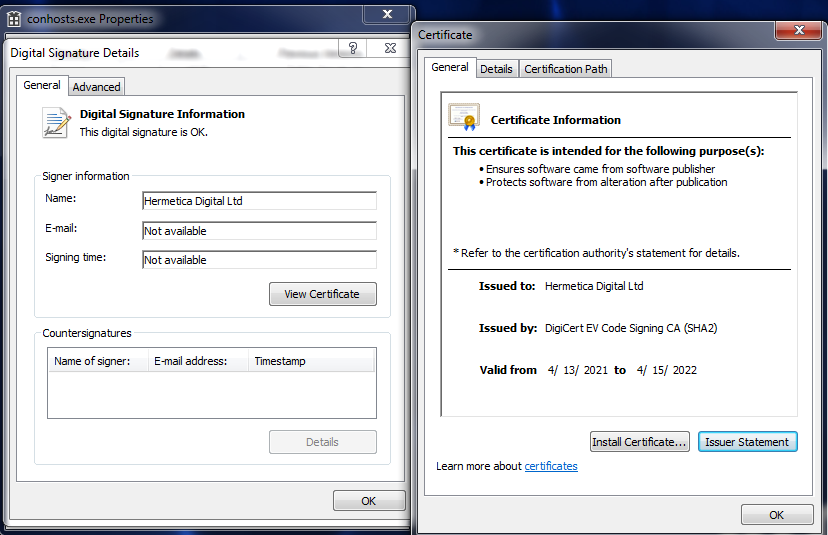
At the start and in due course of the execution it looks for the following privileges:
- SeShutdownPrivilege
- SeBackupPrivilege
- SeLoadDriverPrivilege
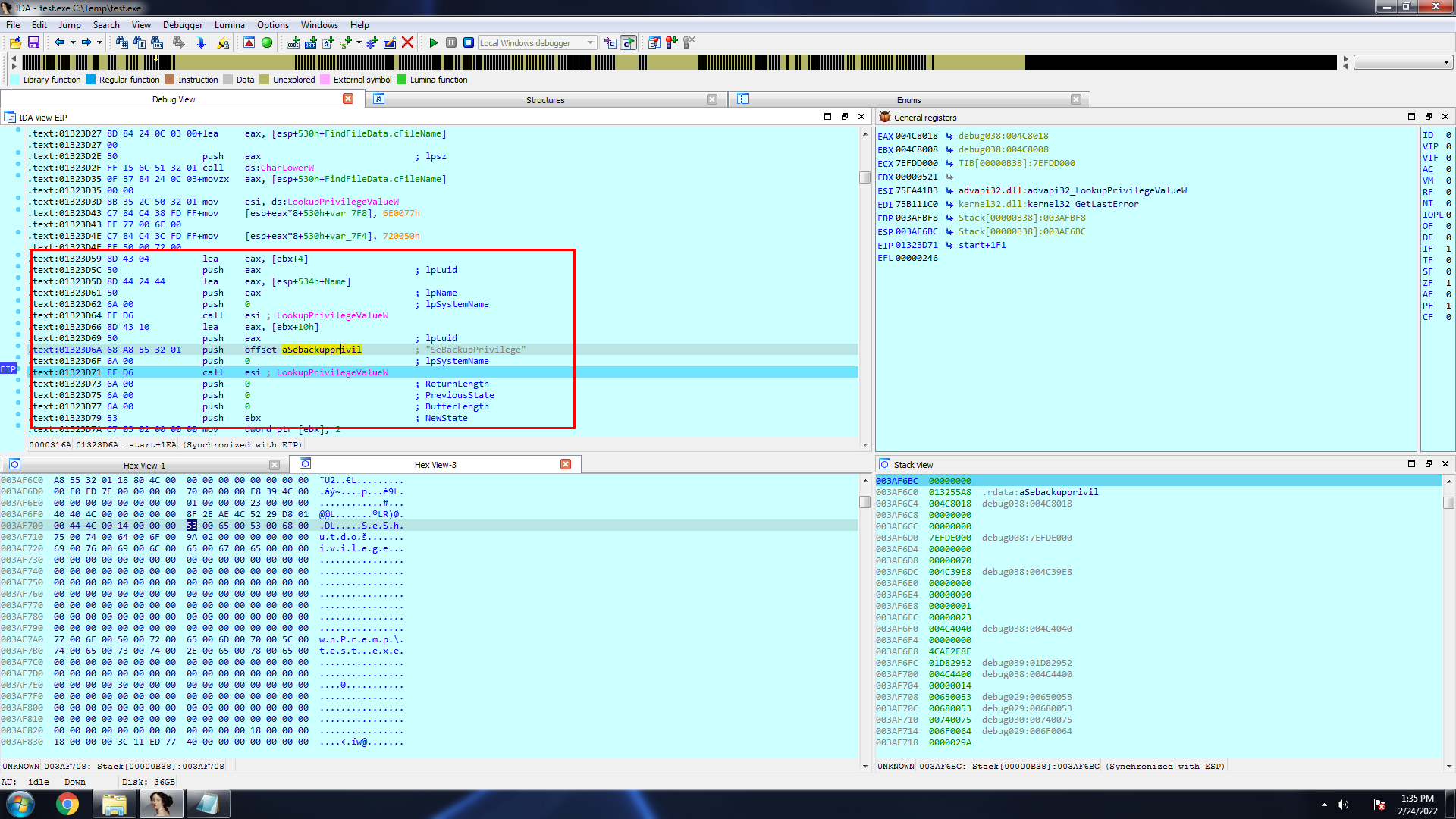
The malware sample then identifies the operating system architecture and depending upon that loads the relevant driver.

If the malware is running on x64bit system it uses Wow64DisableWow64FsRedirection windows API to disable file system redirection so that the sample can copy the driver file in the %system32%\Drivers folder.
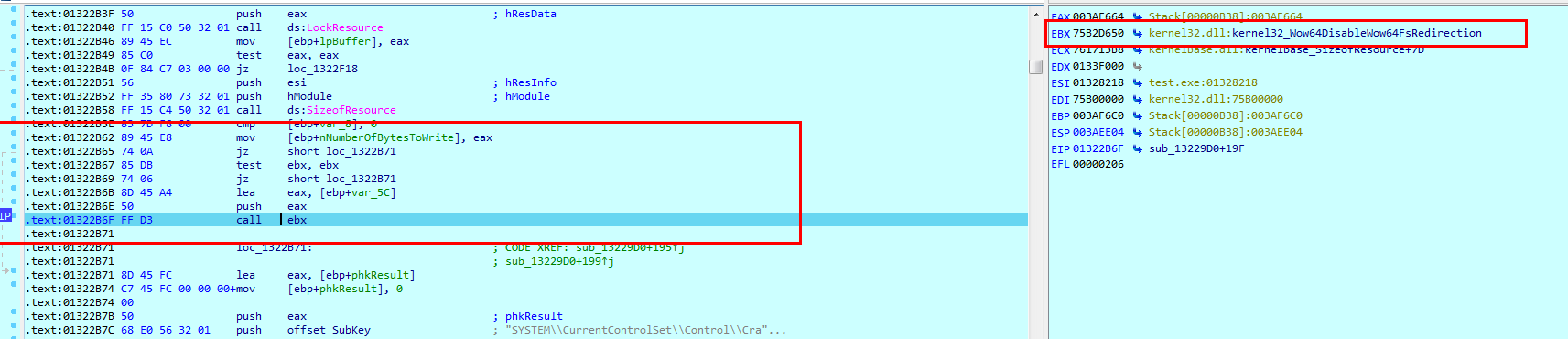
This malware’s resource section contains EaseUS Partition Manager drivers.
These are legitimate drivers associated with EaseUS Partition Master application which is a free partition software. These driver files are compressed by the Lempel-Ziv algorithm.
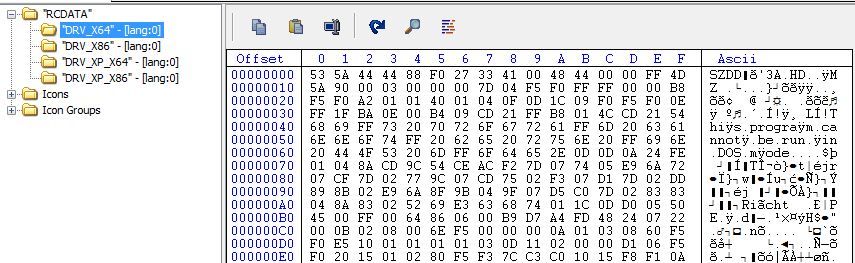
The malware enumerates the registry key SYSTEM\CurrentControlSet\Control\CrashControl and sets the value of CrashDumpEnabled form 2 (default value) to 0 so that Windows does not record any information in the memory dump file.
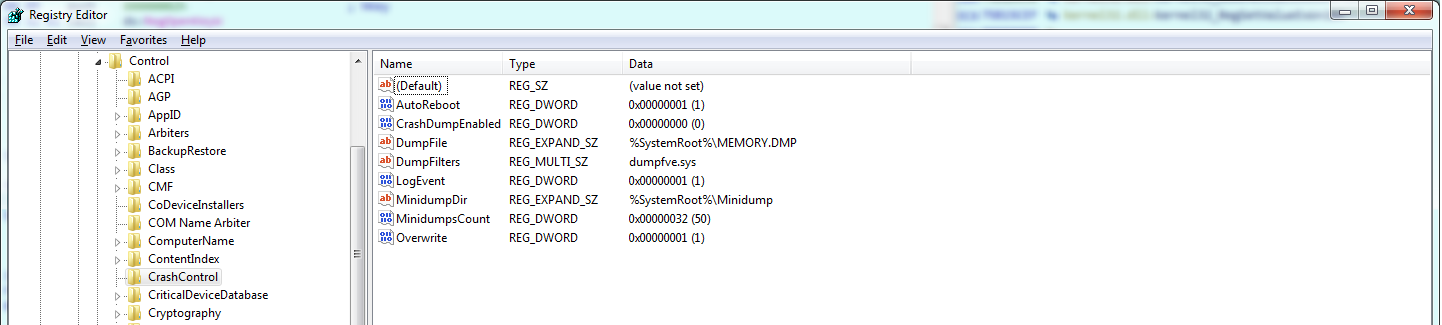
The malware drops the driver file in the %System%\Drivers folder and using SeLoadDriverPrivilege loads the driver.

It then uses the CreateServiceW and StartServiceW to load the driver as a Service.

The malware establishes connection with service control manager using OpenSCManager API and using OpenServiceW and ChangeServiceConfigW, it disables the VSS service (Volume Shadow Copy Service). This service is used to back up the application data.

The malware enumerates the physical drives starting from 0-100 and for each physical Drive \\.\EPMNTDRV\ device is called for a device number.

The EaseUS partition manager driver epmntdrv.sys is then used to access physical drives directly as well as getting partition information through specific IOCTLs.
The malware corrupts the first 512 bytes, the Master Boot Record (MBR) for every Physical Drive. It then waits for all sleeping threads to complete before initiating a reboot. And once the system is rebooted the missing OS prompt is displayed leaving the system unusable.

SonicWall RTDMI engine – part of Capture ATP – has a proactive 0-day protection against this malware.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: HermeticWiper.A (Trojan)
- GAV: HermeticWiper.A_1 (Trojan)





